In this article
In this article, we’re going to dive headfirst into the nitty-gritty of setting up a cyber security risk register, a must-have for any business that’s serious about protecting its digital assets.
A cyber security risk register is essentially a document that helps organisations take a good hard look at the cyber threats they’re facing and figure out a plan to tackle them.
The beauty of a risk register is that it’s a centralised list of all the threats you’re dealing with. It spells out each risk, its chances of happening and how it’ll affect you, as well as what controls are in place to prevent it, who is responsible for dealing with it and what you’re planning to do to sort it out.
By keeping everything in one simple place, you get a clear view of what you’re up against and can make a solid plan to tackle the real problems.
With a well-maintained register and by that, we mean one that you actually use – you can actually get a head start on potential cyber-attacks, track how you’re doing on remediation and steadily start to shrink your organisation’s exposure to online threats.
Implementing a cyber risk register offers several key benefits:
Get a Clear View of Your Risks
A risk register gives you a crystal-clear idea of the cyber landscape facing your business. Everything from asset value to patchwork security measures – its all-in-one place so stakeholders can get a good understanding of the threats and what needs to be done to tackle them.
This increased visibility means your teams can communicate and collaborate more effectively, all while working together towards a common goal of protecting your business.
Prioritise Your Risks
You only have so many resources at your disposal, and it’s up to you to decide where theyre best used. A well-maintained risk register lets you prioritise risks based on how likely they are to happen and how much damage they could do. This way you can make sure the biggest threats get the attention they need.
Make Informed Decisions
A cyber risk register gives you the insights you need to make smart decisions about your risk management strategy. By quantifying risks and looking at the potential impact on your business, you can make an informed call on how to best mitigate them.
This data-driven approach to risk reduction helps you to strike the right balance between security and operational efficiency – and means you can invest your resources in the things that matter most.
Stay on the Right Side of the Law
Many industries are subject to specific cyber security regulations and standards, such as GDPR, HIPAA, PCI DSS and more. Keeping a risk register helps show that you’re taking the necessary steps to manage cyber threats and that helps keep you compliant with the rules.
Stay ahead of cyber risk
By tracking the changing threat landscape, you can refine your risk strategy and keep the business cyber secure.
Understanding Cyber Security Risks
At its core, a cyber security risk is any potential threat that could compromise the confidentiality, integrity, or availability of an organisation’s information systems, data, or networks. These risks are diverse and can originate from a wide range of sources, including malicious actors, system vulnerabilities, human error, or even natural disasters.
By recognising the different types of cyber security threats and their potential impact on your organisation, you can better appreciate the importance of maintaining a comprehensive cyber risk register as a key component of your overall risk management strategy.
Common cyber risks
- Data breaches: Exposure of customer, financial or intellectual property data.
- Unauthorised access: Attackers or misuse of credentials gaining entry to systems and information.
- Malware: Malicious software that disrupts, damages or provides backdoor access.
- Phishing: Deceptive emails or messages that trick users into revealing credentials or installing malware.
- Denial of Service (DoS): Flooding services or networks to make them unavailable to users.
- Insider threats: Risks from employees, contractors or partners with legitimate access.
The consequences are real, from financial loss to reputational damage and reduced customer trust. A clear view of these risks lets leaders prioritise treatments, strengthen controls and reduce exposure.
Steps to Create a Cyber Security Risk Register
So how do you create an effective cyber risk register? It’s all about following a few key steps to ensure you’re tackling your cyber threats head on.
Identify Your Assets & Vulnerabilities
First things first, you need to identify the key assets your business relies on – this could be anything from hardware and software to data and networking gear. Next, you need to pinpoint vulnerabilities that could be exploited by cyber threats.
This is where vulnerability assessments, penetration testing and regular security audits come in. By conducting these tests, you can get a clear picture of the risks your business is facing.
Assess Risk Probabilities & Impact
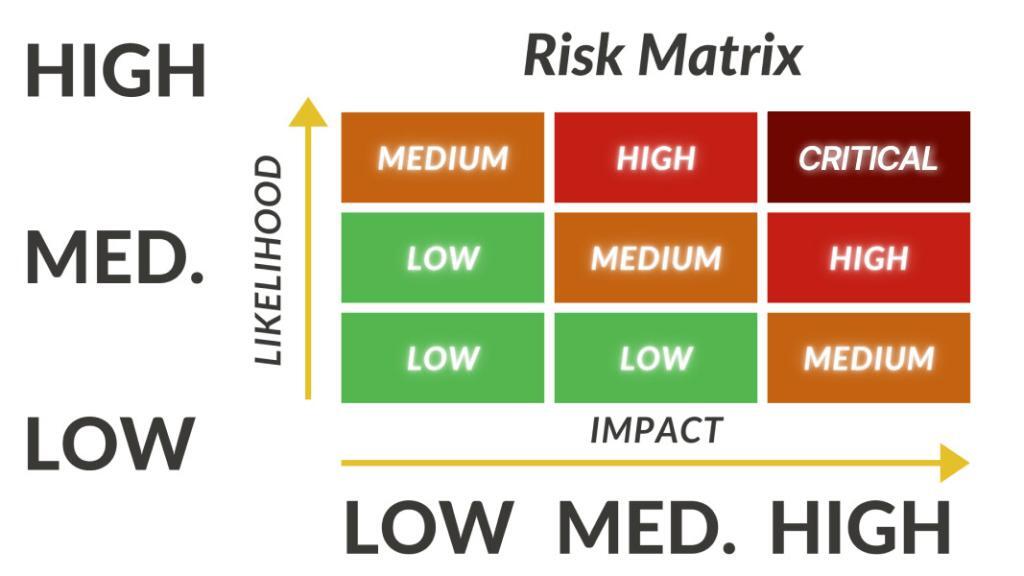
After you’ve hunted down your assets and vulnerabilities, the next step is to use a risk matrix to figure out how likely each risk is to come to fruition. This entails having a good hard think about how probable it is that a threat will make use of a specific vulnerability and what the damage will be to your organisation.
Things to bear in mind when assessing risk probabilities include the risk owner, the state of the threat landscape at the moment, how effective your existing security controls are and how appealing your organisation might be as a target to cyber crooks.
Prioritise Risks Based on the Size of the Hit
Once the likelihood of a risk is figured out, you can prioritise them using a risk priority scale. The ones with a high probability of happening and with a big potential impact should be top priority, while the ones with a lower chance of happening and less severe consequences can be looked at a bit later on.
Prioritising risks enables you to allocate resources more efficiently and ensures that the most critical operational risks get looked at first.
Work out what you need to do to Tackle those Risks
Once the risks have been prioritised – we can stop worrying about what might go wrong for now & get moving on what to do about it – the next step is to start thinking about some strategies that will help you really tackle them. These strategies might involve putting some new security controls in place, updating a few of the ones that are a bit out of date or bringing together a plan for what to do if things go wrong.
The aim here is to make it either so unlikely that a risk actually happens or at least make sure that if it does, the damage will be as minimal as possible. And it’s really important to make sure your mitigation strategies line up with your organisation’s overall security stance & business priorities.
Assign Some Ownership and Responsibilities
To make sure that your mitigation strategies get put into place properly, it’s vital to assign some ownership and responsibilities. Each risk should have a designated owner who’s going to oversee the implementation of mitigation measures and keep an eye on how well they’re working.
You should also clearly define the roles and responsibilities for all the stakeholders who are involved in the cyber security risk assessment and risk management process, including IT staff, management and end users. This gets people to take responsibility and helps keep a proactive approach to managing cyber risks.
Keeping a culture of continuous improvement with your cyber security team is key to success.

Some Best Practices for Your Risk Register
After you’ve created a comprehensive cyber risk register, it’s essential to keep it effective over time. Just like the digital landscape is always changing, so too must your risk register. If you follow some best practices for maintaining your cyber security risk register, you’ll be able to keep it providing accurate, up-to-date information and ensure your organisation stays one step ahead of emerging threats and vulnerabilities.
Spending time and resources on cyber security compliance standards and regularly updating and refining your risk register helps to keep a proactive, resilient approach to managing cyber risks and protect your organisation’s critical assets and reputation.
Get Other People Involved
Get IT staff, management, lawyers and other relevant departments involved in the risk identification and assessment process. When you work together, you can make sure all potential risks are considered and the register reflects the organisation’s collective knowledge.
Keep It in Line with What You’re Trying to Achieve
Make sure your risk register is aligned with your overall business objectives, taking into account how cyber risks might affect your operations, reputation, financial performance and compliance. You should prioritise mitigating cyber risks based on how much they might disrupt or get in the way of achieving those goals.
Regular Reviews, Updates & Feedback
Conduct regular reviews and updates to re look at the likelihood and impact of the risks you’ve identified and to see if there are any new risks on the horizon. Also, make sure to get feedback from other people to check whether your mitigation strategies are working as well as they should be and to see where you can improve.
Use Automation Tools
Make use of automation tools, such as risk assessment software, vulnerability scanners and incident response platforms, to make the risk management process easier, to keep things consistent and to get more accuracy. Just pick tools that integrate well with existing systems and give you the customisation and control that you need.
Following these best practices helps organisations keep an effective cyber risk register, makes informed decisions about risk mitigation strategies, allocates resources effectively and improves overall cyber resilience.
Common challenges and how to address them
Implementing and maintaining a useful cyber risk register is not trivial. Here is a frequent hurdle and practical ways to overcome it.
Lack of resources or expertise
Smaller organisations may not have dedicated cyber staff or budget for consultants.
- Upskill your IT team
Invest in short courses and create simple internal playbooks so knowledge sticks. - Leverage your peer network
Join industry groups and forums to swap templates, lessons learned and benchmarks. - Use cost-effective tooling
Start with open-source risk assessment tools or engage a managed security provider for fractional expertise. - Prioritise the highest risks
Focus limited time and budget on the top issues first, using a clear risk matrix and owners.
Finding it Difficult to Put a Number on Risks
It can be really tough to estimate the likelihood and potential impact of cyber risks. This often involves trying to work out the probability of future events and what the consequences will be.
- Use a consistent risk assessment framework that defines clear criteria for likelihood and impact ratings.
- Leverage industry benchmarks, threat intelligence and historical data to inform your risk assessments.
- Get other people involved from different departments to bring different perspectives on possible impacts.
- Use risk assessment tools that provide guidance and templates for quantifying risks.
Getting People to Adopt New Practices
Sometimes people aren’t willing to adapt to new practices or adopt new ideas.
- Do some proper stakeholder engagement to make sure everyone understands what you’re trying to do and why.
- Communicate the benefits of the new practices or ideas and get people to see how they’ll benefit.
- Lead by example and show people that the new practices or ideas are worth adopting.
- Provide training and education to help people understand the new practices or ideas. Implementing a cyber risk register is likely to require changes to the way things are currently done, and that can be a tough sell to employees or stakeholders who may not see the point of all this.
- Get the word out on why a risk register is a good idea and how it fits in with the overall goals of the organisation – it’s not just some added extra, it’s actually necessary.
- Get some buy-in from stakeholders by involving them in the development process. That way they feel like they’re a part of this and not just being told what to do.
- Give people the tools and training they need to take on their roles and responsibilities when it comes to the risk register.
- Celebrate the wins and share the good news – that way people are more likely to get on board with the risk register.
Balancing Risk Mitigation with Business Needs
Dealing with cyber risks often means implementing new security measures or controls, but those may well get in the way of business as usual.
- Work out which risks are the biggest worry and then line up your mitigation strategies to fit with the organisation’s goals.
- Chat to the business side about what they’re looking for in terms of risk assessment – they’re the ones who know the ins and outs of how things work around here.
- Think about the overall cost of taking on a new risk management strategy – not just the upfront cost but any potential downtime too.
- Keep checking in on how things are going and make sure your risk mitigation strategies are still working and still in line with what the business needs.
By being proactive about the common challenges you’ll face when trying to set up a proper risk register, you should be able to overcome the obstacles and get your organisation in a good place.
Just remember that building a strong risk management culture is a long game – it takes time and effort from everyone right from the top to the bottom.
A Secure Future with Minimal Cyber Risk
These days in the world of cyber security, you can’t just hope for the best – you need a proper risk register to help you identify potential risks, assess them and manage them. By prioritising the big risks and putting your resources into the right places, you can seriously cut down the chances of your organisation getting hit.
We’re really keen on you starting your own risk register and using the tips from this post to get it up and running – and to make things a bit easier for you, we’ve got a TechBrain branded risk register template that you can download and mess with to fit your organisation’s needs.
Building a good risk management culture is all about working together and staying vigilant – keep an eye out for potential security threats, keep your risk register up to date and make sure you’re getting input from all the right people.
We here at TechBrain are all about helping organisations navigate the cyber security minefield – if you need help with anything from setting up a risk register to meeting compliance standards or just generally getting a handle on cyber security, we’re here to help.
So, what are you waiting for? Get in control of your cyber risks today and start building a safer future for your organisation – with a bit of help from TechBrain of course.