In this article
When it comes to making the most of a cyber security certification, it’s crucial to understand the risks that come with non-compliance. We all know the stories – data breaches, system failures, reputational damage and financial losses are all too common for Aussie businesses to ignore.
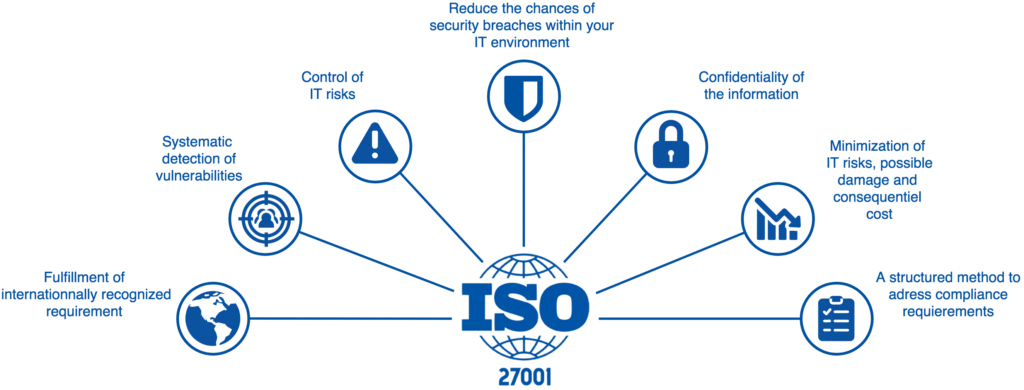
Having the peace of mind that your business is on the right tracks is key, which is why we’ll be looking at the key components of an Information Security Management System (ISMS) and how it can keep your business one step ahead of evolving cyber threats, thanks to the internationally recognised ISO 27000 series.
The ISO 27000 bunch of standards developed by the International Organisation for Standardisation (ISO) and the International Electrotechnical Commission (IEC) lays out a pretty comprehensive framework for getting an ISMS up and running, and keeping it that way.
By going with these standards, businesses can get the confidence and security they need to thrive in this increasingly digital age, knowing that their sensitive info is properly protected against all sorts of evolving cyber threats.
What is an Information Security Management System (ISMS)?
An information security management system (ISMS) is basically a strategy to keep on top of the information security threats lurking inside your company.
ISMS’s cover a whole range of policies, procedures and controls that are designed to safeguard the confidentiality, integrity and availability of your information assets, all while lining up with your organisation’s business goals, legal and regulatory requirements.
The key components of an ISMS
Policies & Procedures
These are the documented guidelines that set out how info security is managed within the organisation. You’ll find things like roles and responsibilities, acceptable use policies and incident response plans all in there.
Risk Management
It’s a systematic process for figuring out, assessing and dealing with information security risks, all taking into account your organisation’s specific context and risk appetite.
Asset Management
All about identifying, classifying and protecting your organisation’s info assets – hardware, software, data and intellectual property – the lot.
Access control
This is about making sure only the right people have access to sensitive info and systems – and it’s all based on the principle of least privilege.
Incident Management
These are the procedures for detecting, responding to and recovering from info security incidents – like data breaches or system failures.
Business Continuity
It’s about having plans and procedures in place to guarantee that your organisation’s key info systems and services are always available, even in the face of disaster.
Compliance
All about making sure the info security procedures of the company are following industry standards and best practices, as well as relevant legal and regulatory standards.
The Business Case for Implementing an ISMS
Investing in an ISMS isn’t just about compliance or risk management – it also makes good business sense. You get benefits like a competitive advantage and enhanced customer trust, all the way through to improved efficiency and reduced costs associated with security incidents. The business case for implementing an ISMS is pretty clear.
Competitive Advantage
Showing a commitment to info security can really help an organisation stand out from the pack and win the trust of customers and partners who value the protection of their sensitive data.
Improved efficiency for your business
An ISMS can help simplify and get your organisation’s information security processes up to speed, so you don’t have to waste time with unnecessary duplicated effort and can make the most out of the resources you have to play with.
Better decision-making
With a clear view of where your organisation stands with its infosec risks and the effectiveness of its controls, an ISMS can give you a solid foundation to make better decisions no matter where you sit in the business.
Reducing costs in the long run
Putting an ISMS in place does require a decent upfront investment, but it can actually help protect you from the huge costs that come with a security breach – lost productivity, all those expensive legal fees, and just generally tanking your reputation.
Increased Resilience
An ISMS can help businesses prepare for and respond to info security incidents more effectively, minimising the impact on operations and keeping critical systems and services up and running.
Managing IT best practices is a must for ensuring compliance with ISO 27001 standards and protecting sensitive data across various industries.
Organisations have to follow the Australian Privacy Principles (APPs) under the Privacy Act 1988 which sets out standards for the collection, use, disclosure and storage of personal information. In healthcare, the My Health Records Act 2012 sets out the requirements for the privacy and security of electronic health information. And financial institutions have to comply with the Australian Prudential Regulation Authority (APRA) Prudential Standard CPS 234 which focuses on info security management.
By lining up their practices with ISO 27001 and these industry-specific regulations, businesses can show their commitment to info security, stay on top of compliance and build trust with customers and stakeholders.
Real-world examples of successful ISMS implementations like those at Fujitsu show just how real the benefits can be when you adopt an ISO 27001-compliant approach to info security.
ISMS Frameworks & Security Controls
A number of ISMS frameworks have been developed to help organisations get info security practices into place. Some of the most popular ones include:
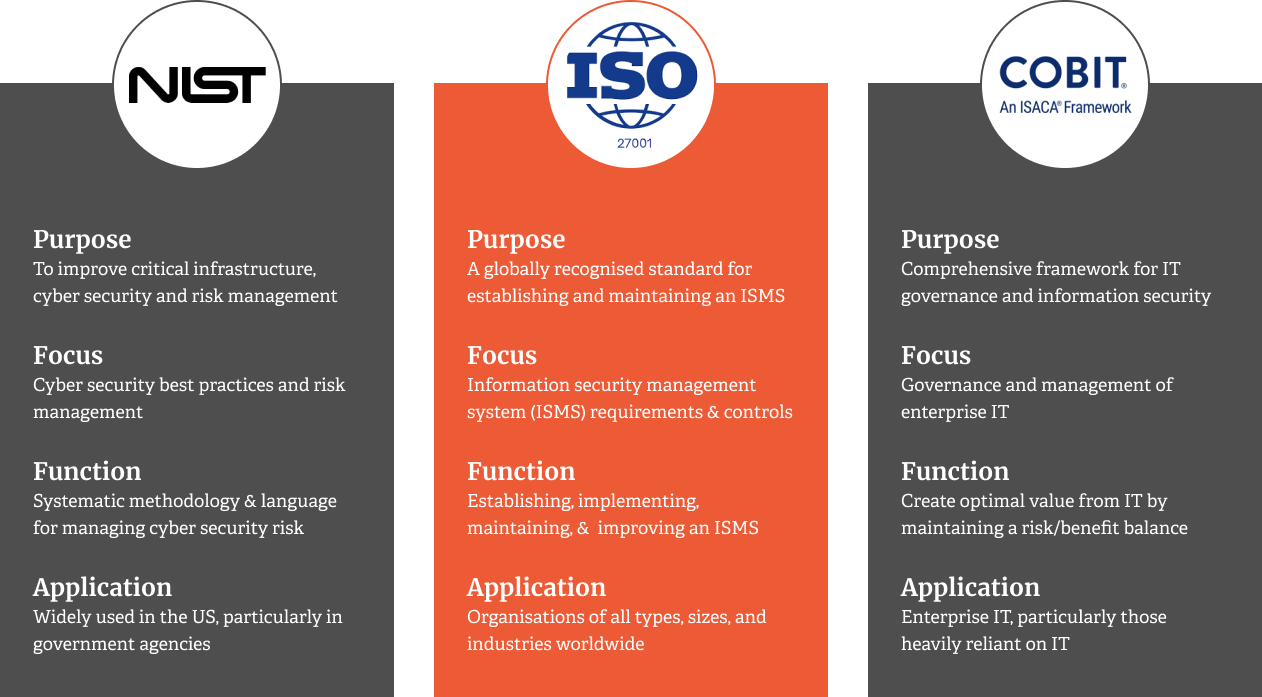
ISO 27001
The international standard for an Information Security Management System (ISMS) provides a comprehensive set of requirements to help you establish, implement, maintain, and continually improve your ISMS.
NIST Cybersecurity Framework
In the US, the National Institute of Standards and Technology developed a voluntary framework to help organisations manage and reduce their cybersecurity risk.
COBIT
ISACA developed a framework for IT governance and management, including information security aspects.
At the heart of these frameworks are security controls, which serve as the first line of defence to protect the confidentiality, integrity and availability of your information assets from unauthorised access, modification or disclosure.
These security controls come in three main flavours:
- Administrative Controls: these are the policies, procedures, and guidelines that define how information security is managed within your organisation.
- Technical Controls: this is the bit where hardware, software and network mechanisms protect information assets from unauthorised access or modification.
- Physical Controls: this is all about protecting physical assets, like data centres, servers, and workstations, from theft, damage, or unauthorised access.
You should also give some thought to the physical and environmental security controls you need to protect physical areas, equipment and facilities from unwanted attention.
The ISO 27000 Family of Standards
The ISO/IEC 27000 family of standards gives you a really solid starting point for building an ISMS, each standard tackling a specific bit of information security management in its own way. The ones you’re most likely to be interested in as a business are:
ISO 27001
This is the main event, the flagship standard that tells you exactly what you need to do to set up, run, and continually improve your ISMS.
ISO 27002
A straightforward guide on how to put the security controls in place that ISO 27001 talks about – it’s basically a code of practice that shows you some pretty good ways to do it.
ISO 27003
This standard gives guidance on the implementation of an ISMS, including the planning, design and implementation phases.
ISO 27004
This standard provides guidelines on how to monitor, measure, analyse and evaluate the effectiveness of your ISMS.
ISO 27005
This standard gives you guidelines on how to manage information security risk, including cyber risk assessment and risk treatment.
ISO 27006
This standard sets out the requirements for bodies providing audits and certifications of ISMS, to ensure consistency and credibility in the certification process.
ISO 27007
This standard gives you guidelines on how to conduct ISMS audits, so you can assess whether your ISMS is conforming to the requirements of ISO 27001.
By understanding what each standard is all about, you’ll be able to navigate the ISO/IEC 27000 landscape more effectively and pick out the ones that are most relevant to your specific cybersecurity needs & objectives.
Implementing an ISO 27001 Compliant ISMS
Implementing an ISMS compliant with ISO 27001 is a big task that involves defining boundaries, securing management buy-in, establishing a project team, conducting risk assessments, selecting and implementing security controls, documenting policies, procedures, records, monitoring effectiveness and continually improving.
Here’s a general roadmap to help you through it:
- Scoping & Planning: figure out where you’re going to draw the line on your ISMS, get leadership on-board & the resources you need, and form up a team to oversee the whole project.
- Risk Assessment: take stock of what security risks are lurking in your organisation, bear in mind the business landscape, laws & regulations, & what your customers expect from you.
- Control Selection & Implementation: pick the right security measures for you and get them set up, based on the risk assessment, and taking into account your organisations appetite for risk and what you can realistically afford to do.
- Documentation & Communication: Get the policies, guidelines and records sorted out that you’re going to need to keep everything running smoothly, and make sure all relevant stakeholders are in the loop about what’s expected of them.
- Monitoring & Review: This is the part where you keep tabs on whether your ISMS is actually working, invite in auditors, keep an eye on performance and get feedback from others so you can drive continuous improvement. Don’t forget about handling any security incidents that do come up – you need to know how to respond fast, communicate effectively, and make sure they don’t happen again.
- Continual Improvement: Keep your ISMS up to scratch by regularly reflecting on how the business is changing, new risks and opportunities that pop up, and what your customers & other stakeholders are saying.
By following this roadmap and using the guidance provided by the ISO 27000 standards, you can implement an ISMS that’s tailored to your specific needs and helps you manage your information security risks more effectively.
Benefits of Working with an ISO 27001 Specialist?
If you don’t have the in-house expertise or resources, implementing an ISO 27001 compliant ISMS can be a real challenge. That’s where experienced ISO 27001 specialists like TechBrain can help out, especially during the ISMS audit phase.
Expert Guidance
ISO 27001 specialists have deep knowledge of the standard and its implementation, and can provide expert guidance and support throughout the ISMS journey.
Accelerated Implementation
With an ISO 27001 specialist on board, you can speed up the implementation process and get your ISMS up and running faster.
By tapping into the kinds of techniques that have been proven and widely adopted across the industry, ISMS specialists working to the ISO 27001 standard can really help businesses get their ISMS up and running in no time – and at a lower cost, to boot. That’s a much faster and more cost-effective way to get everything sorted.
Reduced risk
Our team can help spot and mitigate those info-security risks that are lurking in the shadows, and reduce the chance of a security incident from happening in the first place. We’re also keen to stress just how important it is to keep on top of relationships with suppliers and partners, to make sure they’re all on board with good info-security practise.
Ongoing support
We also provide ongoing guidance and support to help businesses keep their ISMS running smoothly over time, and make sure it stays relevant and effective in the face of all the new challenges and risks that keep popping up.
By actually working with an ISMS specialist, businesses can take a lot of the pain out of getting an ISMS up and running in the first place, and start to see some real benefits out of having a solid info-security posture a lot sooner.
Safeguard Your Data & Protect Your Reputation with an ISO 27000-compliant ISMS
The ISO 27000 family of standards gives you a solid foundation for setting up, implementing and keeping an ISMS running smoothly.
By following the guidelines in the ISO 27001 standard, Australian businesses can keep their sensitive data safe and sound, keep up with all the regulatory requirements, and keep the customers happy.
Implementing an ISMS can be tough at first, but the end benefits are obvious – and the trouble is, that’s where a lot of businesses start to struggle. But when you work with a specialist like us at TechBrain, we can really help you navigate all the complexities of an ISMS implementation, and get you started on the road to better info-security.