In this article
The “it’ll be alright” era of security has finally come to an end.
For years, Australian businesses have stuck with a “castle-and-moat” security model. We built a strong fortified perimeter, otherwise known as a firewall around our offices and assumed that everything inside from the CEO’s laptop to the reception printer was safe.
But with hybrid work, multi-cloud environments and more and more sophisticated supply chain attacks, that old “castle” has gone. The walls aren’t as secure as they used to be. And the “castle” isn’t even in one place anymore. The end user’s data, devices and identities are all moving back and forth between the office, their home and the cloud.
The old way of thinking just isn’t working anymore. We used to rely on the network perimeter and on-premises infrastructure (in the office) to keep us safe. But with distributed environments and the flexibility of hybrid work, that’s just not enough. Zero Trust addresses this problem by saying that we should never assume someone’s safe to access our systems just because they’re inside the network.
It all began with one simple question: Can we really trust our networks anymore? This basic scepticism led John Kindervag at Forrester Research to coin the term ‘Zero Trust’ in 2010.
Since then, his concept has been the driving force in the modern security environments we have today.
Key Takeaways
- The old security model is broken. Hybrid work and cloud migration have made traditional “castle-and-moat” firewalls obsolete.
- The core philosophy is simple: Zero Trust isn’t a product, it’s a strategy based on the idea that you should never trust, but always verify.
- The business benefits add up: Zero Trust makes it harder for hackers to get in and spread, which cuts the cost of a ransomware attack and keeps your business running.
- The implementation process is gradual, focusing on Identity, Devices, Networks, Applications and Data.
- In Australia, Zero Trust is the way to go. It gives you a framework to implement the ACSC Essential Eight and meets ISO 27001 requirements.
If you’re still relying on trusting your internal network to keep you safe, then you’re currently using an outdated map. These days, the modern standard is Zero Trust Architecture (ZTA), as championed by NIST and the Australian Cyber Security Centre (ACSC).
Zero Trust has come a long way from its early days as a perimeter-based model, and is now a whole new way of approaching security. It’s not just another product to buy. It’s a fundamental shift in thinking.
Let’s explore what Zero Trust means for your business and how to implement it without disrupting business continuity.
As Australian businesses adopt cloud and modern technologies, Zero Trust has become a practical way to manage risk without ripping everything out. It focuses on securing users, devices, and access using tools organisations already trust, like Microsoft 365.– Ashish Srivastava
What is Zero Trust Architecture?
Zero Trust is a modern cyber security framework that’s built on one simple idea: Never Trust, Always Verify.
It needs strong identity and access management (IAM) controls to let only people who are genuinely allowed to access systems and data. And that includes devices and applications.
In old networks, users would log in and have free rein to access files and apps. In a Zero Trust environment, that’s not possible. The system continually asks questions to determine whether a user is who they claim to be, whether their device is up to date, and whether they really need access to what they’re asking for.
Identity and Access Management (IAM) verifies every user, app and machine by using multifactor authentication, single sign-on and behaviour analysis.
Whether a user is coming from the office in Perth or a cafe in Bali, the system asks the same questions before letting them access any specific resource:
- Who are you? (ID verification)
- Is your device up to date? (Patch status/Compliance)
- Do you need this file right now? (Least Privilege)
- What’s your role and what permissions do you have? (Assess user role and permissions as part of the access request process)
The Three Core Principles
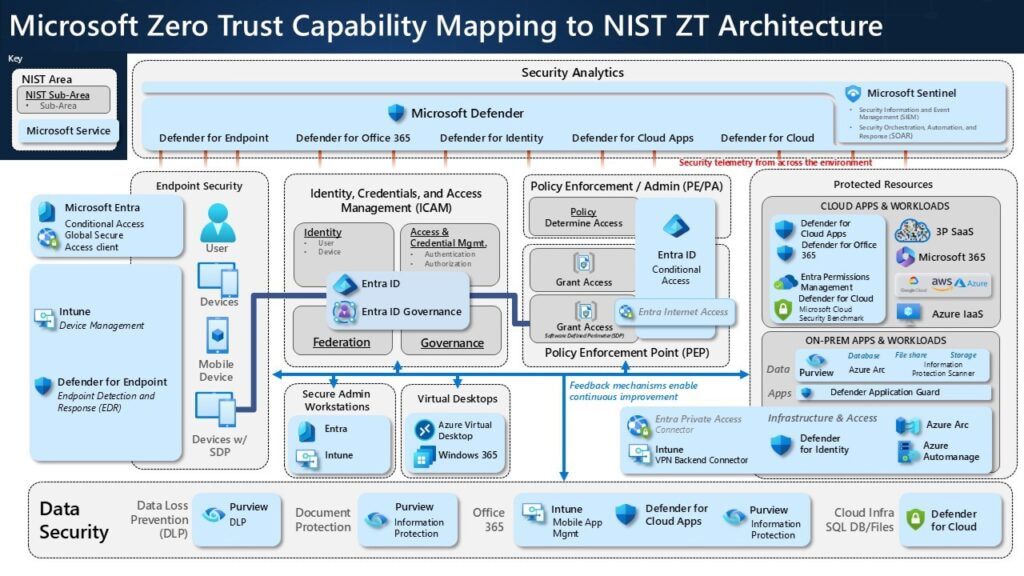
Aligning with NIST SP 800-207 and Microsoft’s popular model, the three pillars of ZTA are:
Verify Exactly What You Need
We make decisions based on all the available data points, not just a password. We need to know where the login is coming from, whether the device has the latest virus protection and whether the user has the right permissions. And we’re not just talking about passwords; we’re talking about multifactor authentication and single sign-on to make sure we’re talking to the right person.
Use the Least Amount of Access
We don’t give users more access than they need. We don’t want a manager who only needs to get to the company manual to be able to get into the company’s accounting system. We want the least amount of access that’s possible, so that even if someone does get in, they can’t get to what they really want.
Users only get access to the specific apps they need, just for as long as they need them, that’s commonly referred to as Just-In-Time access. This limits the damage that can be done if someone’s credentials get lost or stolen. Every access request gets checked over and we enforce our trust policies to make sure we’re granting only the rights that are absolutely needed at the time.
Assume Breach
Design your network like an attacker has already gotten a foot in the door. This shifts focus to limiting the fallout via micro-segmentation, so a hacked laptop doesn’t end up compromising the whole network.
Zero Trust & The Essential Eight
We get asked all the time by Australian CIOs: “Do I go Zero Trust or the Essential Eight?”
The answer is both. Think of Zero Trust as the big-picture architecture, and the Essential Eight as the basic standard.
Zero Trust Architecture provides the framework that makes the Essential Eight controls work properly when you’re dealing with a modern network where the perimeter has gone. Zero Trust wraps multiple security controls across the network which minimises the attack surface & risk by restricting access and keeping breaches contained.
| Essential Eight Control | In a Traditional Network | In a Zero Trust Architecture |
| MFA | Checked once at VPN/Desktop login. | Continuous Verification: Checked dynamically. If a user tries to access high-value data, they are re-prompted. |
| Restrict Admin Privileges | Admins have permanent “God mode” access. | Just-In-Time (JIT): Admin rights are granted only for the minutes required to do a specific task, then revoked. |
| Patch Applications | Scheduled scans and manual updates. | Device Posture Gating: A device is automatically blocked from accessing corporate data if it is missing critical security updates. |
With the changes to the Privacy Act and the tightening of the Security of Critical Infrastructure Act (SOCI), “good enough” just isn’t any more. Zero Trust is the only architecture that’s resilient enough to deal with these modern threats and give the defence in depth that regulators are looking for.
By building in multiple layers of security, you can limit the impact of a breach, making sure that even if one layer gets cracked, there are plenty of other controls in place to contain the damage and keep the overall risk down.
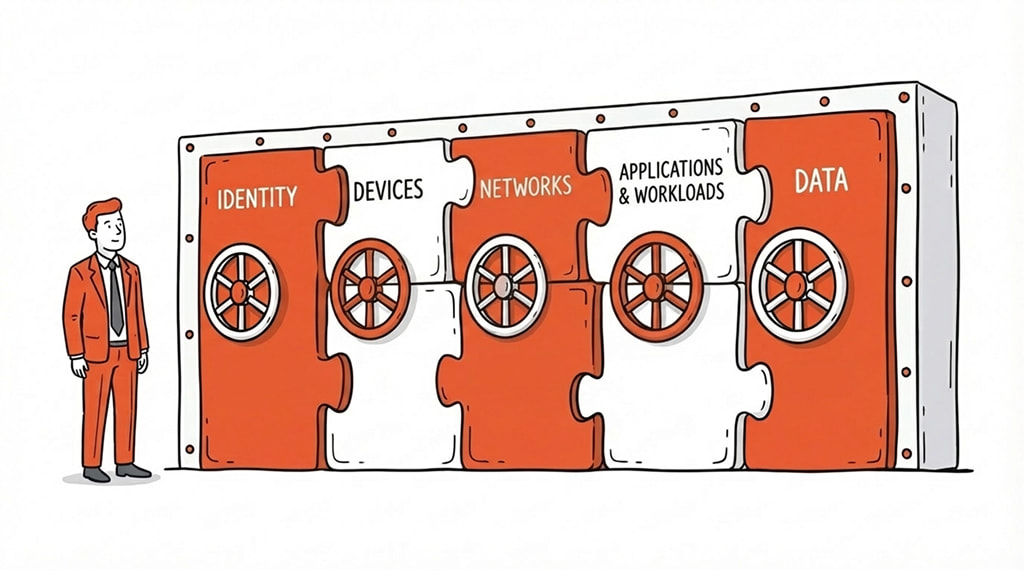
Navigating the Framework: The 5 Pillars
You don’t buy “One Zero Trust, please.” You build it across your ecosystem.
Implementing Zero Trust is a phased rollout of technology that works smoothly with your existing network setup. The CISA Zero Trust Maturity Model breaks this all down into five key areas that are widely used in Australia.
Identity (The New Perimeter)
We don’t just check the password – we verify the user. Using tools like Microsoft Entra ID, we enforce strong authentication & risk-based policies.
Your identity is the foundation because if you don’t know who’s actually on your network, you can’t secure it. Before you grant access, you need to verify the user’s identity & the device they’re using, to make sure only people you trust can get in.
Comprehensive identity management means you need to know all the different identity sources within the organisation, and manage them. Monitoring user activity is a big part of identity-based security, to detect any suspicious behaviour and keep the system running smoothly.
Key Control: Phishing-resistant MFA and Conditional Access policies that check the risk in real-time.
Devices
We don’t just trust a device because it’s company-issued. We verify its health on the fly.
Has the firewall got turned on? Has the OS got the latest patches? If not – no access. Endpoint security is key in checking device compliance & integrity before granting access, making sure only trusted endpoints can get to sensitive resources.
Key Control: If your EDR spots malware, the Zero Trust policy immediately revokes access to email & files.
Networks
Traditional networks are “flat” which means if you get in, you can just move around & ping any server. In these environments, attackers or unauthorised users can get at resources all over the network, no problem. Zero Trust breaks the network up into tiny, secure zones – that’s the foundation of a zero-trust network.
Agent-Based Segmentation: Instead of using expensive hardware firewalls, we put a software agent on every server. This agent acts as a personal bodyguard, only letting the server talk to the apps it actually needs.
The Benefit: If ransomware gets one server, it can’t spread. It’s trapped in that one “micro-segment”, which really limits the blast radius. Micro-segmentation is essential in a zero-trust network to limit lateral movement, ensuring if an attacker gets in, they can’t just roam all over the place.
Applications & Workloads
This is probably the biggest shift for remote work, and it’s an area where you really need to modernise.
The Old Way (VPN)
A user connects to a VPN concentrator. They are now “on the network” and can theoretically scan for other devices. It creates a “trust tunnel”.
The Zero Trust Way (ZTNA)
The user authenticates to a cloud broker. The broker checks their identity and device health. If they pass, the broker creates a single, encrypted tunnel just for that one specific application such as Jira or SAP.
In contrast to traditional VPN-access arrangements, Zero Trust Network Access (ZTNA) gives you more secure, context-aware access, reducing the attack surface and stopping would-be attackers moving laterally across the network.
Data
And then we get to data – classifying and encrypting it. Even if files are stolen (“exfiltrated”), they should be unreadable unless the keys are there. Protecting data is crucial both as it moves around and when it’s stored, to ensure that any stored information is encrypted to stop it being accessed by people who shouldn’t be looking.
Key Control: Data Loss Prevention (DLP) and Rights Management – keeping an eye on data and controlling who views it.
Zero Trust by Sector: Australian Use Cases
Zero Trust isn’t a one-size-fits-all approach. Here’s how it applies to key sectors in Australia.
Federal Agencies
Australian federal agencies are at the front of the pack in adopting Zero Trust frameworks to boost their cyber security, following US government guidance and advice from NIST, CISA, and DISA.
Mining & Resources
If you’re in the mining business, you’ve got a whole lot of risk when OT and IT networks start to converge. If a hacker jumps from the company email system to the network controlling those autonomous haul trucks, safety is compromised.
The ZT Fix: Micro-segmentation is used to put a “digital air gap” between IT and OT networks. Even if the corporate network is breached, the hacker can’t get across the boundary to impact site operations.
Healthcare
When doctors move between hospitals and private clinics, often using their own iPads (BYOD), you can’t really “trust” the device.
The ZT Fix: The hospital doesn’t trust the iPad. It trusts the doctor’s identity (verified via MFA) and sends patient data to a secure, containerised web session that leaves no data on the device.
Financial Services & Legal
Under strict APRA CPS 234 and Privacy Act obligations, protecting client data is paramount.
The ZT Fix: Data-centric policies. Documents are encrypted with “Rights Management.” Even if a lawyer accidentally emails a sensitive contract to the wrong person, that person cannot open it because they cannot authenticate against the policy server.
Zero Trust & Compliance: ISO 27001 and SOCI
For Australian executives, compliance is often the driver for budget. Zero Trust directly supports your compliance posture, especially if you are preparing for an ISMS ISO 27001 audit where access controls are scrutinised.
ISO 27001:2022 Mapping
If you are pursuing ISO 27001 certification, Zero Trust architecture ticks’ multiple boxes in the new Annex A controls:
| ISO 27001:2022 Control | Zero Trust Alignment |
| A.5.15 Access Control | ZTA moves from static rules to dynamic, risk-based access policies. |
| A.8.1 User Endpoint Devices | ZTA enforces device health checks before granting access known as Device Posture. |
| A.8.12 Data Leakage Prevention | ZTA includes DLP policies to block sensitive data from leaving trusted apps. |
| A.5.29 InfoSec during Disruption | ZTA’s “Assume Breach” resilience ensures operations continue even during partial compromise. |
SOCI Act Alignment
For critical infrastructure providers, the SOCI Act requires a Risk Management Program. Zero Trust’s comprehensive visibility, achieved by logging every access attempt, directly supports the “Enhanced Cyber Security Obligations” for incident detection and response.
Zero Trust Implementation: A Practical Roadmap
Moving to Zero Trust is a journey rather than a switch flip. At TechBrain, we advise a phased approach to avoid user friction.
Phase 1: Define the Protect Surface
Don’t try to boil the ocean. Identify your “Crown Jewels” such as customer data (subject to the Privacy Act), IP, or financial systems. This is your Protect Surface which is much smaller than your total attack surface.
Phase 2: Map Transaction Flows
You can’t protect what you can’t see. We audit how data moves. Who accesses the payroll system? Which API talks to your CRM?
Phase 3: Architect the Zero Trust Policy
We build rules based on the “Kipling Method” of Who, What, When, Where, Why and How.
- Example Policy: “Marketing Managers (Who) can access the CRM (What) only from compliant devices (How) during business hours (When).”
Phase 4: Monitor and Maintain
Zero Trust requires constant telemetry. We monitor logs to look for anomalies like a user logging in from Sydney and Singapore within the same hour which is known as Impossible Travel.
Cloud & Hybrid: The New Network Perimeter
In our experience auditing Australian networks, cloud misconfigurations are just the latest problem to show up.
Zero Trust gives you a way to secure your cloud and hybrid environments without worrying about traditional network boundaries. Instead, it keeps on checking to see if you can trust what’s coming in, no matter where it’s coming from. That’s where you need a good cloud security posture management breakdown to help you figure out where all the hidden dangers are.
Implementing Zero Trust on AWS, Azure or Microsoft 365 is all about changing the way you think.
Here are a few key things to remember:
- Service Accounts are Users too: Any non-human identities like APIs and scripts need to have the “Least Privilege” rule applied to them just like humans do.
- Tags & Labels: Use Attribute-Based Access Control (ABAC). So rather than letting a VM through because it has a certain IP address, let it through if it has a certain tag like “Project Alpha”.
Common Challenges (and How to Overcome Them)
-
Legacy Applications
- The Problem: Old accounting software doesn’t do MFA.
- The Fix: Use secure application proxies or Zero Trust Network Access (ZTNA) connectors to stick modern authentication in front of the old app. So even if all you can do is use MFA before you even log in, it’s better than nothing.
-
User Pushback
- The Problem: MFA is just a pain in the neck.
- The Fix: Use adaptive authentication. So, if you’re sitting in the office on a work device, you might not be asked for your MFA. But as the risk goes up (because you’re working from a cafe or on a new device), then you get asked. To balance security with user experience, we often recommend revisiting your enterprise password policy to ensure it aligns with modern identity protocols rather than outdated rotation rules.
-
Budget & Complexity
- The Problem: This all sounds really expensive.
- The Fix: Chances are you’ve already got most of the tools you need. If you’re on Microsoft 365 Business Premium or E3/E5 you’ve got the core identity and device management engines you need to get started.
The Castle Has Fallen: Securing the Post-Perimeter World
Australian businesses are facing a really tough time when it comes to cybercrime costs which means the cost of doing nothing is actually higher than the cost of doing something.
Zero Trust isn’t about distrusting your staff – it’s about protecting them. It moves the security burden off the user and onto the architecture, so the less likely your company is to get taken down by a single phishing click.
It all sounds really complex, but that’s a good thing. If you’re one of the many businesses that’s tempted to just do it all on your own, don’t worry you don’t have to. Working with a managed security service provider is a great way to get the expertise you need.
Ready to move beyond the perimeter?
Get in touch with TechBrain and we’ll do a maturity assessment for you. We’ll compare your current setup against the Essential Eight and ISO 27001 standards, and then build a roadmap that secures your future.
Sources
- NIST SP 800-207: The global standard defining Zero Trust Architecture. Link
- CISA Zero Trust Maturity Model: A guide for implementing the five pillars of Zero Trust. Link
- ACSC Essential Eight: Strategies to mitigate cyber security incidents. Link
- ISO/IEC 27001:2022: Information security, cyber security and privacy protection standards. Link