In this article
What is IAM and how does it work?
Identity and Access Management (IAM) makes sure the right people get to the right resources at the right time. Managing access rights, adding and removing people and enforcing security policies are some of the main tasks of IAM.
Proper identity management lets businesses automate the process of adding and managing users, which makes things run smoother and reduces the chance of human error.
Authentication verifies a user’s identity by comparing their login credentials to an identity management database. Precise authorisation then decides what they can do. IAM tools manage user identity and access rights automatically. Multifactor authentication (MFA) adds an extra step to the process of verifying a user’s identity by forcing them to do so in a different way.
IAM is needed for organisations to control access to a lot of user information such as personal info and preferences. Putting all your IAM functions on one platform makes it easier to manage and see what’s going on.
Standards you will encounter
- SAML and OpenID Connect for single sign‑on between apps and your identity provider
- OAuth 2.0 for delegated, scoped access to APIs
- SCIM for automated provisioning and deprovisioning
- WebAuthn and FIDO2 for phishing‑resistant MFA and passkeys, increasingly supported in Australia’s guidance for secure accounts
Organisations need to choose an IAM approach, considering best practices and standards, to be able to grant and manage access for all user identities and resources. With more users accessing apps from different locations and devices, IAM frameworks are crucial.
Organisations that implement IAM need to know how accounts are provisioned and deprovisioned to maintain security and reduce insider threats. Strict provisioning reduces the risk of an insider threat.
The single control that cuts BEC risk in the first month in our experience is enabling Multi-factor Authentication across all business critical, sensitive information including personally identifiable information [PII].
– Ashish Srivastava
Risk and compliance in Australia
Identity sits at the centre of Australia’s privacy and security expectations. Under APP 11 you need to take reasonable steps to protect personal information, and be able to show what you did. ISO 27001 pushes in the same direction by requiring controlled access, timely deprovisioning and evidence that reviews actually happen.
IAM tools can facilitate compliance by providing an audit trail history of permissions authorisation, removal, and delegation.
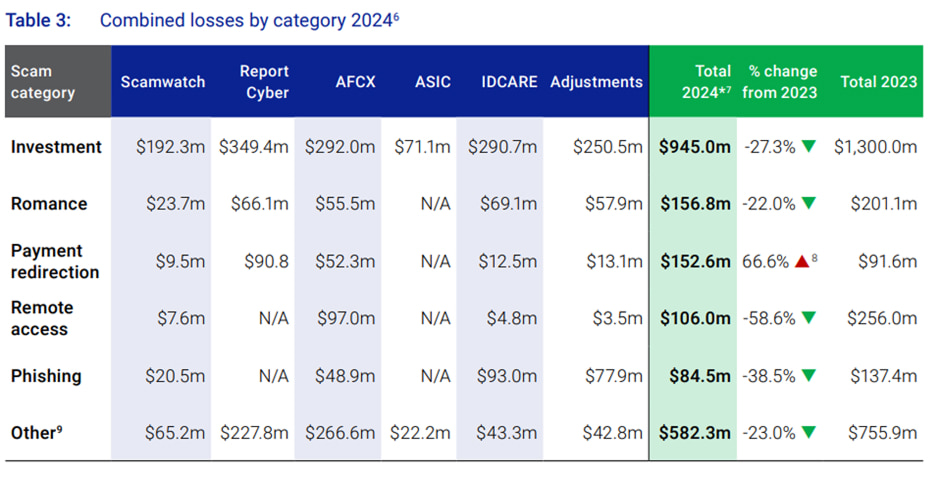
Major Risk Factors
Payment redirection is a major threat to Australian businesses. NASC data says $152.6 million in 2024, with small business reporting $13.1 million in total scam losses to Scamwatch and false billing the most reported category.
Protecting sensitive data and confidentiality is key to preventing attacks on financial information and reducing risk of unauthorised access or data breaches.
On card payments, AusPayNet recorded $688 million in card‑not‑present fraud in 2023, now over 90 percent of all card fraud. The domestic CNP fraud rate dropped to $1.06 per $1,000 since the CNP Framework, but overseas CNP fraud is about ten times higher, which argues for adaptive policies and transaction‑level risk signals, especially for organisations selling online.
Evidence from the public sector shows why the basics matter. The NSW Audit Office reported that only 31 percent of Protect-domain controls were fully met, third-party incidents tripled, and 59 percent of agencies lacked independent assurance over their compliance assessments.
Use these findings to justify a focus on fundamentals and third-party access controls. Defining a clear IAM strategy aligns controls with business goals, risk tolerance and regulatory requirements.
What to demonstrate to auditors and customers
- Multi-factor authentication coverage for users and admins, with legacy authentication blocked
- A documented Role-Based Access Control (RBAC) model and time-bound privileged access
- Joiner-mover-leaver automation with clear deprovisioning timestamps
- Scheduled access reviews for high-risk apps and roles, with revocations recorded
Credential misuse and payment redirection continue to drive incidents locally, so pair IAM controls with basic finance workflow checks. For example, require step-up authentication for supplier or bank detail changes, and monitor mailbox rules in finance and executive mailboxes.
Quick wins that reduce risk and produce evidence
- Enforce phishing-resistant MFA for admins and finance first, then expand to the wider workforce
- Put your top 5–10 apps behind SSO and retire basic auth to cut token theft paths
- Pilot PAM for tenant and domain admins with approvals and session recording so you can show how privileged actions are governed
If third-party access is in scope, treat suppliers as first-class identities: least privilege, expiry dates and session monitoring. That one change often closes a compliance gap and removes noisy findings.
IAM vs identity security vs PAM vs IGA vs ITDR vs CIAM
| Capability | Primary scope | Where it helps first | Typical owners |
| IAM | Authentication, authorisation, SSO, lifecycle | MFA coverage, SSO rollout, JML automation | IT operations, security |
| Identity security / ITDR | Detect and respond to identity‑layer threats | Risky sign‑ins, impossible travel, token theft, session takeover | SOC, security engineering |
| PAM | Secure admin and service accounts, vault secrets, just‑in‑time elevation and session control | Reduce admin risk, record privileged activity | Infrastructure, security |
| IGA | Requests, approvals, access reviews, SoD checks and certification | Compliance evidence, least‑privilege hygiene | Risk, audit, security |
| CIAM | Customer identity for portals and apps | Consent, privacy, scalability for consumers | Product, privacy, marketing |
The ACSC Essential Eight maturity updates highlight phishing-resistant MFA and tighter patch timeframes which span IAM and identity security. Use E8 for prioritisation, then implement with your IAM stack.
When choosing IAM tools, companies must consider many aspects and challenges including privacy, security and compliance. Organisations need to evaluate different IAM products and providers to ensure the chosen solutions meet the needs of every department in the company. IAM affects every department and type of user within an organisation.
Solving these challenges helps organisations implement identity and access management across all users and systems.
Core IAM capabilities to get right first
Authentication
Use MFA as default and introduce passkeys for your highest risk roles first. Biometric methods such as fingerprint and face are increasingly used to authenticate users and modern IAM systems can detect anomalies in login behaviour to ensure only authenticated users gain access.
Authorisation and access privileges
Start with RBAC for simplicity then add ABAC for context such as device health, location or contractor status. Access policies determine what actions users are allowed to perform based on their job, job title and responsibilities. This ensures each user only has the permissions required for their specific job functions.
Least privilege should be your default. Keep admin roles small in number and time-bound.
Federation and SSO
Use SAML or OIDC to centralise trust and simplify user experience. Identity federation involves setting up identity providers (IdPs) and service providers (SPs) to establish trust and secure authentication between systems.
Identity federation allows multiple systems to share user access, so users can log in based on authenticating against one of the systems in the federation. Prioritise your top 5 to 10 applications by risk and usage so you can consolidate policy quickly.
Joiner-mover-leaver (JML)
Automate joiner-mover-leaver processes from HR to directory to apps using SCIM where possible. Orphaned and over-privileged accounts are a common root cause in incidents and audits. Lack of proper deprovisioning can expose organisations to insider threats and external attacks.
Detailed audit capabilities can ensure users’ access changes accordingly when they switch roles or leave the organisation.
Access reviews and certification
Run quarterly reviews for high-risk apps and privileged roles, and annual reviews for lower-risk systems. Measure revocations raised and time to close as KPIs.
Identity proofing and recovery
Use reliable identity proofing for remote onboarding and step-up authentication for sensitive changes such as bank details and password resets. Provide self-service recovery guarded by strong factors and approvals.
Machine and service identities
Treat non-human identities seriously. Inventory service accounts, keys, certificates and tokens. Rotate secrets, adopt vaulting and enforce least privilege for automated jobs and CI/CD. Adaptive authentication methods in IAM can enhance security by analysing user behaviour and location to detect anomalies.
The use of APIs and machine identities is a growing trend within IAM to manage non-human interactions requiring access control. This area is increasingly visible in competitor content and audit findings and it’s where silent lateral movement happens.
The biggest challenge we see in the initial MFA adoption curve is due to change resistance. To accelerate it, we recommend foundational adoption by leadership and high-risk users. This simple approach leads to reducing risks related to MFA significantly, and direction to the rest of the organisation to follow suit.
– Ashish Srivastava
Operationalising IAM with your SOC & IT team
Admin model and access management
Harden admin accounts, enforce change windows for high-risk policy edits and test break-glass accounts quarterly. Managing privileged access is critical to secure high-level permissions and prevent unauthorized actions by administrators or attackers.
Signals to forward to your SOC
Risky sign-ins, impossible travel, token theft indicators, privilege elevation, mailbox-rule creation, consent grants to high-risk apps, mass downloads or deletions.
If you want identity‑driven detections, TechBrain’s Managed SOC services can watch the signals that matter.
Runbooks to practice
Lock account, revoke sessions and refresh tokens, force reset and re-enrol, offboard user or contractor, rotate keys and certificates for service accounts.
Third-party access
The NSW report highlights weaknesses in third-party oversight. Apply least-privilege to suppliers, restrict from unmanaged devices where possible and monitor their sessions like your own.
TechBrain’s SOC receives a huge number of logs every day, while all logs are scrutinised and evaluated, some of the genuine high value identity signals we end up actioning are multiple failed MFA attempts, privilege escalation outside approved workflows, and bypassing security controls.A lot of noisy signals are also analysed but don’t end up with an action such as normal password resets, isolated failed login attempts that are followed up with successful login with MFA.
– Ashish Srivastava
Metrics executives care about
By tracking these metrics, you’ll learn valuable insights about your security posture and where to improve.
Coverage
- Phishing-resistant MFA users
- Apps behind SSO
- MTTD on exit
Risk
- Legacy auth attempts blocked
- Privilege elevation approvals and denials
- Access review revocations raised and closed
Outcomes
- Fewer help desk password resets and lockouts
- Fewer duplicate or orphaned accounts
- Fewer BEC attempts leading to payment holds
The key IAM metrics that we see mattering to boards are: Privilege Access review aligned to the Essential Eight maturity model, IAM hygiene such as Password age, stale credentials, and privilege access.
– Ashish Srivastava
Common mistakes to avoid
- Over-allocating admin roles or leaving standing privilege in place
- Stale guest accounts and orphaned service accounts
- MFA without recovery paths or pilot groups
- Ignoring contractors and short-term staff in policy
- Buying IGA before you have SSO, JML and PAM basics working
- Weak oversight of third-party access
90-day IAM roadmap
This 90-day roadmap is a practical guide to implementing IAM, outlining actions to establish an identity and access management program.
Days 0–30
- Disable stale and duplicate accounts, decide on the RBAC model for core roles
- Draft an access review cadence and define evidence needed for APP 11 and ISO 27001
Days 31–60
- Put your top 5–10 apps behind SSO, starting with finance, HR and collaboration
- Roll out passwordless or phishing-resistant methods to administrators and finance first
- Start a PAM pilot for tenant admins, domain admins and network devices with vaulting, approvals and session recording
- Automate JML using your HR system as the trigger for provisioning and deprovisioning
Days 61–90
- Run your first access review for high-risk systems and privileged roles
- Harden admin workflows with just-in-time elevation, approvals and session recording
- Stand up a dashboard for coverage and risk metrics, then hand over runbooks to operations
Make identity your strongest control
Strong IAM is how Australian organisations turn cyber risk into routine operations. When most incidents start with credentials, the path forward is clear. Get sign-ins right, keep privileges tight and automate the joiner-mover-leaver cycle so access changes as fast as your business does. Do the basics well and the rest of your controls work better.
Over the next 90 days, aim for visible wins that staff and auditors can feel. Move priority apps behind SSO, enforce phishing-resistant MFA, retire legacy authentication and stand-up simple access reviews for high-risk systems. Measure what matters, publish the numbers and keep improving. That is how you cut breach likelihood, reduce blast radius and remove day-to-day friction.
Ready to turn this into a plan your team can execute? Talk to TechBrain’s Cyber Security team for a tailored IAM uplift and hands-on help with MFA, SSO, RBAC and operational runbooks.