In this article
The Australian Signals Directorate (ASD), which is known for being a leader in national cyber security, has recently put out its Annual Cyber Threat Report for 2024–25. Headlines often focus on raw numbers, but for Australian business leaders, the most important story is how cybercriminals are changing their tactics, not just how often they attack.
At TechBrain, we know that simply pointing to rising cybercrime isn’t enough. It’s more important to know how bad actors are getting better at what they do and why traditional defence strategies are becoming less effective.
The threat landscape is changing all the time, so we need to be on the lookout and be ready to change our plans. The Australian government is working with businesses to make the country more cyber-resilient and deal with these new threats. All Australian businesses and organisations need to improve their cyber defences to keep sensitive data safe and keep their operations running smoothly.
We looked at the report’s technical details to make a summary of how the Australian cyber landscape is changing and what needs to be done in the next year.
The Rising Risk of Malicious Cyber Activity
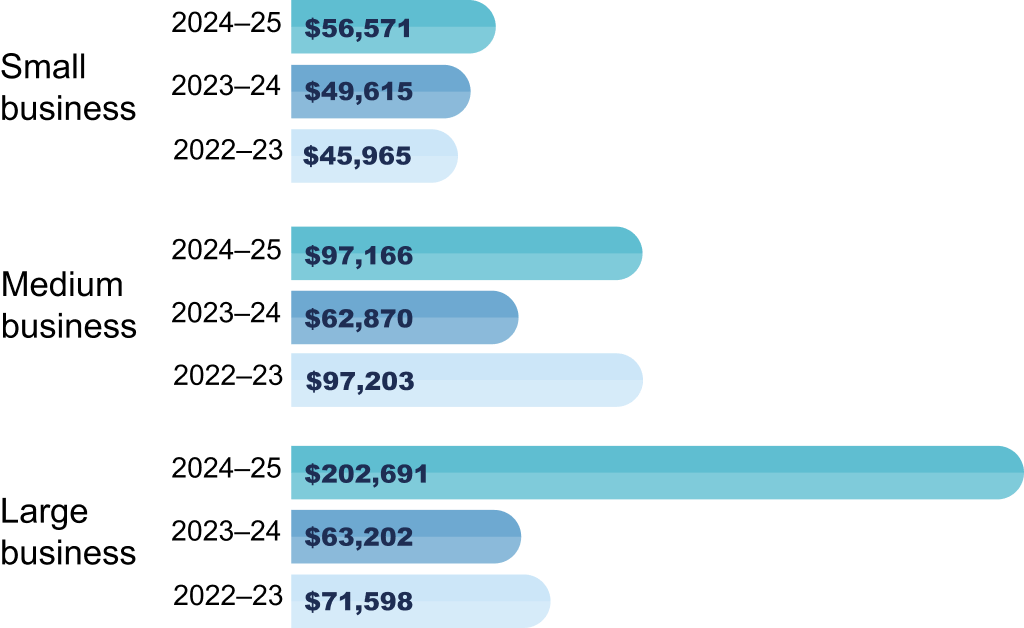
The report shows a worrying trend: the cost of cybercrime is going up faster than the number of attacks. The average reported financial losses show how much of an effect these events have on Australian businesses:
- Small Businesses: The average cost that businesses say they have to pay has gone up 14% to $56,600.
- Medium Businesses: The average loss is now $97,200, which is a 55% rise.
- Big Businesses: The average loss has gone up by 219% to $202,700.
Strategic Insight
ASD links the higher costs are due to both higher ransom demands and the fact that fixing the problem is becoming increasingly more difficult. Attackers are no longer just encrypting data and leaving; they are now lurking for an extended period of time, stealing large amounts of data, and causing a lot of trouble.
This makes it hard to maintain business continuity during a breach, and these problems can persist for months.
The ASD highlights the fact that attackers are increasingly targeting financial accounts, through online banking fraud and online shopping fraud, leading to further financial losses and identity theft.
“Living Off The Land” (LOTL) is the New Normal
A major discovery in the 24-25 report is just how common “Living off the Land” methods are.
This shows the increased complexity and long-term thinking threat actors are applying to their attacks, which many small and medium businesses are not ready for. Threat actors use persistent threats and stealing credentials to avoid being caught. They often use stolen login credentials that they bought on the dark web to get into and stay in systems.
This is the reality: many attackers won’t drop obvious malware that traditional antivirus will catch. They’ll use the tools admins already use, like PowerShell, remote management, identity tooling, scripting, legitimate binaries and hide in normal traffic.
Making it harder to detect malicious cyber activity as attacker tactics evolve.
The Gap in Authority
A lot of businesses use a prevention-first approach with simple tools like antivirus. But the ASD report makes it clear that these attackers could go undetected until they cause significant damage if behaviour isn’t actively logged and watched.
It’s important to keep an eye out for potentially harmful online activity and report cyber incidents right away. Blocking a legitimate tool won’t work if you can’t see how it’s being used. Finding and responding to cyber incidents quickly is important for maintaining security and lowering risk.
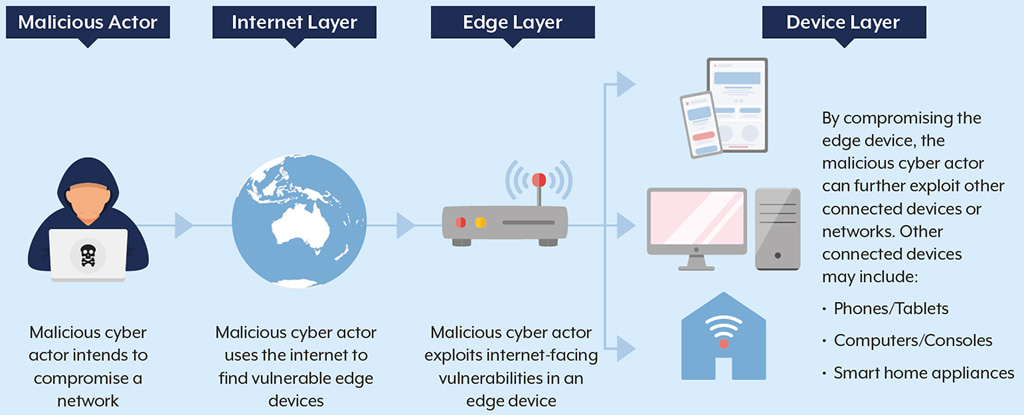
Edge Devices are a Weak Point
The report says that cybercriminals are specifically going after edge devices like VPN concentrators, routers and firewalls.
The ASD found more than 120 incidents that targeted these devices, and 96% of them were successful. Malicious actors look for operational weaknesses in critical infrastructure networks, as well as other important networks and target networks run by Australian government agencies, critical infrastructure, and private sector organisations. These networks are especially vulnerable.
These edge devices are located at the edge of the network and are often “set and forget” parts that don’t get the quick patching cycles that other hardware does.
Our Analysis
Edge devices can fail badly if they aren’t kept up with a strict patching schedule. Attackers use these weaknesses to launch disruptive attacks on specific organisations, and in the worst cases, they can even stop Australia’s most important services from working.
MFA is Not a One-Size-Fits-All Solution
Even though the industry supports Multi-Factor Authentication (MFA), data from 2024-25 shows that standard MFA is becoming less effective against advanced threats.
Phishing kits and “adversary-in-the-middle” attacks are becoming more common. These attacks break into corporate networks and let hackers steal data, access systems without permission, and launch ransomware attacks.
Once attackers get in, they often use that access to further compromise corporate networks and launch more attacks, which makes their reach and impact bigger.
Our Insight
MFA is no longer just a simple step to meet requirements. MFA’s protection is reduced unless it is phishing resistant. If attackers get hold of credentials, they can use them to make future attacks easier on corporate networks, which raises the risk of ongoing compromise.
Stop treating MFA as just a one-off project and start viewing it as an identity program:
- Top priority for executives, finance and IT.
- Audit and remove any weak factors where possible.
- Tie conditional access to risk (device health, location, session risk, impossible travel, token theft signals).
Identity is the New Perimeter Not the Office Firewall
Info stealing malware has changed the focus from office firewalls to how employees act in their personal lives. This malware steals saved passwords from web browsers, usually on personal devices used for work, and sends them to brokers on the dark web.
Attackers use these tools to steal sensitive data, like personally identifiable information (PII), which they then sell or use on the black market. This lets them get into personal accounts, social media, and financial services without having to hack systems directly.
In-effect, an attacker doesn’t have to hack a system; they can just log in as a real user.
Our Insight:
A change in culture and technology is needed. “Shadow IT” is a big security hole.
Companies need to use conditional access policies that check not only the user’s password but also the device and the situation of the login attempt.
Important Lessons for Your 2026 Cyber Strategy
The ASD report says that 2025 was a year when “adversaries adapted.” To stay strong in 2026, businesses need to change their strategies from passive prevention to active resilience.
Shift spend from “more tools” to “more visibility”
Build a security monitoring capability that actually delivers:
- Who logged in from where and on what device.
- What privileged actions were taken.
- What changed and what data got moved.
That usually means tightening up logging across identity, end points, servers, M365, network, and key SaaS, then centralising it (SIEM/XDR) with alerting and response capability.
Sharing intelligence with law enforcement partners also enhances effective security monitoring and response.
Close the “Edge” Gap
Given the ASD’s findings, edge security needs its own rules. On top of all that, organisations need to be aware of the risk of potential disruptive attacks, as state-sponsored hackers might target critical infrastructure to cause some serious disruption.
- Patch windows and change control that match the threat landscape.
- Configuration baselines (remote admin controls, MFA on admin portals, logging sent out).
- Retirement plans for end-of-life gear.
Strong edge security doesn’t just protect against direct threats, it also makes it harder for hackers to host stolen data and facilitate cybercrime.
Plan for the “Assume Compromise”
Plan for containment, identity reset and recovery not just “remove malware”. Make sure you’ve got a plan in place for cyber security incidents and cyber-attacks, and that reporting pathways are understood and tested.
Don’t Wait for a Breach to Set Your 2026 Priorities
The ASD Cyber Threat Report 2024-25 makes it clear that being reactive is dangerous.
The average cost of a cyber-attack for a medium-sized business is now almost $100,000, so doing nothing costs more than investing in resilience. The deeper reality is that adversaries are no longer just breaking in. They are logging in.
They are living off the land, bypassing traditional gates, and weaponising your own tools against you. In recent years, threat actors have relentlessly targeted Australians, demonstrating the persistent and aggressive nature of cyber-attacks against individuals and organisations alike. In this landscape, a defensive strategy built solely on “prevention” is destined to fail.
The shift to “Assume Compromise” is strategic
It means acknowledging that a determined adversary will eventually find a way in. The difference between a minor incident and a catastrophic headline lies in your ability to detect them quickly and recover instantly.
That’s why TechBrain operates differently. We didn’t wait for this report to adapt; our services were built to address the exact threats now highlighted by the ASD. This foresight ensures our clients remain ahead of the curve.
We don’t just patch software; we build defensible architectures.
Our TechSafe managed security service is engineered to counter these specific modern threats by closing gaps in edge devices, hardening identity perimeters, and deploying the visibility tools needed to catch “invisible” intruders.
You cannot control the threat landscape, but you can control your readiness. Contact TechBrain today to benchmark your defences against the 2026 threat landscape.
FAQ
Why is cybercrime costing big businesses more?
The cost for big companies has gone up 219% to more than $202,000. This is because modern attacks are more complicated. Attackers stay in networks longer, steal more data, and make legal and operational problems much worse.
What does “Living off the Land” (LOTL) mean?
Attackers use LOTL to carry out attacks with tools that are already on the system, like PowerShell. Because these tools are trusted, they often let bad things happen that regular antivirus software can’t find.
Is SMS Multi-Factor Authentication (MFA) still safe?
SMS MFA is better than not having MFA at all, but it is not completely safe. “Adversary-in-the-middle” attacks let attackers get around basic MFA. Passkeys or physical security keys are safe options.
What are “Edge Devices” and why are they dangerous?
Firewalls and routers are examples of edge devices that connect private networks to the public internet. They are dangerous because they are harder to fix and are open to the internet. Attacks on these devices have shown alarming success rates in the 24-25 report.
Sources and Further Reading
ASD/ACSC Annual Cyber Threat Report 2024–25 (full report) – Link
ASD/ACSC Annual Cyber Threat Report 2024–25 Fact Sheet (businesses and organisations) – Link