In this article
We all know that Australia is facing the very real threat of increased cyber attacks. And while your average internet user can’t do much against sophisticated malware or DDoS attacks, there is one area where being prepared will put you and your people on the front foot.
And that’s in fighting back against social engineering attacks.
Knowing Your Enemy: Decoding Social Engineering Attacks
Social engineering attacks are a form of hacking. But whereas typical cybercrime relies on computer programs and coding, social engineering targets the mind.
A social engineering attack is a psychological manipulation technique that’s used to deceive or influence its target, tricking the person or organisation into divulging sensitive information, performing a task (such as a payment), or providing access to a secure computer system.
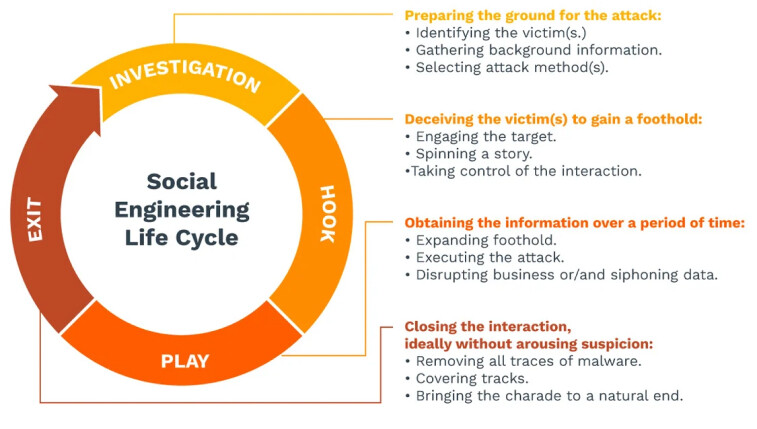
Social engineering attacks work because they take advantage of simple human psychology. The perpetrators will reach out to the intended victim, either through electronic or physical means, and pose as a trusted authority figure or brand. They either build a relationship with the victim, slowly building trust, or they’ll create a sense of urgency that the target feels compelled to act on immediately.
And in an increasingly digital world, the truly pervasive thing about social engineering attacks is that they occur both online and offline—it’s not just an issue that’s relegated to cyberspace.
According to the Office of the Australian Information Commissioner, of the major reported Notifiable Data Breaches from 1 July to 31 December 2022, social engineering attacks accounted for 24% of data breaches caused by cybercriminals. That’s a quarter of all notifiable data breaches.
They’re so prevalent because they’re effective—and it works.
The Human Firewall Remains a Cyber Cornerstone
Social engineering attacks prey on people; so it’s in these same people that we can create robust systems to combat these attacks.
The human element is crucial in building up strong cyber security platforms and practices. Known as the human firewall, teaching your people and providing them with the knowledge and tools to safely and effectively manage their data and systems adds a powerful layer of security to your business.
But building a robust human firewall isn’t just the responsibility of one person, or your lone IT team. It relies on everyone in your organisation being aware of and understanding good data security protocol.
The catch to this is that your people are the weakest link in your cyber security defence. A Gartner survey conducted in May and June 2022 found that 69% of employees surveyed had been found to neglect or break security practices within the past 12 months. But with the right training, ongoing education, and support, you can ensure your people have the power to stop social engineering attacks in their tracks.
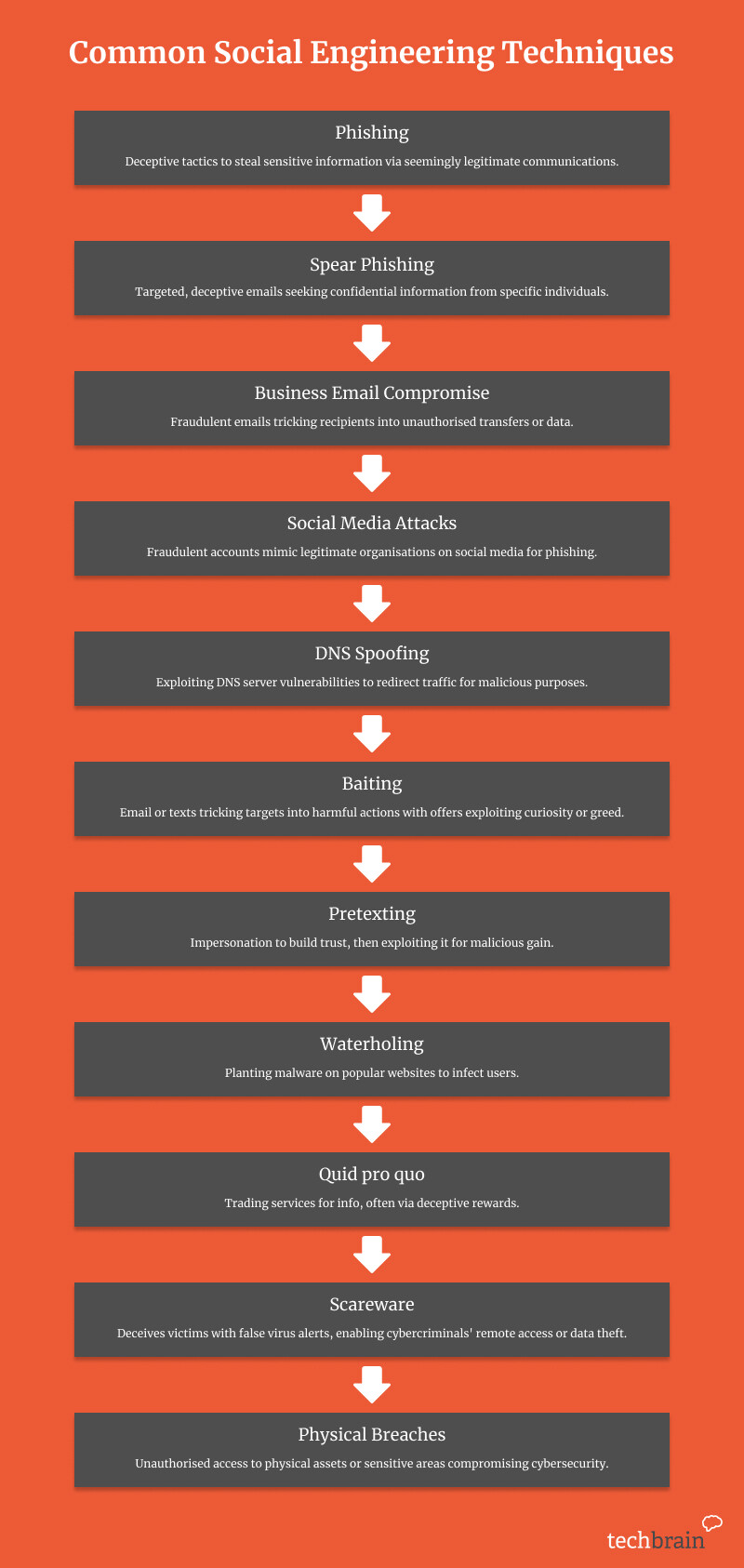
Common Social Engineering Techniques
Social engineering attacks aren’t just one thing. The term covers a wide variety of social engineering tactics, ranging from extremely sophisticated operations to techniques that are astonishing in their simplicity.
Phishing
Phishing is one the most common and well-known forms of social engineering attacks. Perpetrated at a broad scale, cybercriminals will send an email or text to the target, claiming to be from a legitimate source. They’re effectively fishing for information: the text or email will tell the target to click a link, respond with details, or open an attachment, which then either sees the user provide them with sensitive data or credentials, or unwittingly download a malicious file onto their device.
Spear phishing
Spear phishing is the more targeted version of phishing, and goes after specific individuals or organisations. With a spear phishing attack, the perpetrators take the time to do their research and build a legitimate-looking ruse that’s almost undetectable from the real source.
According to security provider Barracuda, spear phishing makes up a minute 0.1% of all email-based attacks, yet the tactic is responsible for up to 66% of all data breaches. It’s a smart tool for cybercriminals, because it’s much harder to identify than simple phishing—and it works.
Business email compromise
Business email compromise (BEC) is an extremely common form of social engineering. Targeted at businesses, BEC attacks see cybercriminals send emails to victims from spoofed email addresses, pretending to be a trusted source, such as another employee or business supplier, and trick them into supplying sensitive information, data, or money.
In 2021-2022, Australia saw an increase in financial losses from business email compromise, rising to over $98 million, with an average loss of $64,000 per incident report.
Social media attacks
A social networking site is a goldmine for social engineering attacks. A form of phishing scam known as angler phishing, social media avenues provide opportunities for social engineers to pose as legitimate organisations, using fraudulent social media accounts to either provide enticing offers to encourage users to their networks or contacting targets directly to seek out sensitive information.
DNS spoofing
DNS spoofing is particularly insidious. This method of attack sees cybercriminals seek out and exploit DNS server vulnerabilities, then use these to diver internet traffic away from legitimate sites and on to fake sites set up by the cybercriminals. Then, when the user types in their credentials, they can immediately log their details, or simply infect their computer with malicious software.
Baiting
Baiting is one of the oldest psychological tricks in the human playbook. Baiting attacks see criminals trick their target into performing an action by using their own curiosity or greed against them.
It’s not particularly advanced in practice. The malicious actor might send a text or email to the target purporting to be a free offer, or with an attachment that appears to be something intriguing, like company payroll details, or contracts. Or it could be as simple as leaving a malware-infected physical media—like a USB drive—in a public place for someone to find, take to work, and insert a malware infected application unwittingly into their computer.
Pretexting
Pretexting is essentially a modern form of con artistry. It sees a malicious actor impersonate a legitimate individual or organisation—such as a company supplier, bank representative, or co-worker—and foster a sense of trust with their target. Then, once the relationship is built, they exploit this trust, uncovering the information or gaining access they need to further attack the company.
Waterholing
Watering hole attacks are a form of cyber attack that infects a popular industry website with malware—effectively ‘poisoning the waterhole’—which then infects any user that lands on the site. It takes a lot of research on the social engineers’ part to find vulnerabilities to exploit, but the far-reaching effects of this type of attack mean that the rewards can be high.
Quid pro quo
Where baiting generally focuses on a physical item or reward, quid pro quo focuses on a service. It’s a form of phishing, where the perpetrator asks for information in exchange for a reward or compensation.
The threat might come in the form of a perceived giveaway, or the offer to participate in research; or it could be malicious threat actors pretending to be an IT company, and trick users into providing login credentials or disabling their cyber security systems momentarily, allowing access.
Scareware
A modern cousin of the old-fashioned pop-up spam, scareware assaults the victim with false alarms or threats of a possible virus infection, and provides a link they can access to download a (fraudulent) tool to neutralise the problem. Clicking the link then installs malicious code onto the target’s computer, providing cybercriminals with remote access to the device. Or it may ask them to provide certain personal details in order to download the tool, which the perpetrators can then use later.
It’s quite prevalent, and you would have seen these types of social engineering tactics used in flashing banner ads telling you that your work or home computer may be infected with spyware, or in emails saying that a bank or personal account has been compromised.
Physical breaches
What sounds like it’s in the realm of an old-fashioned spy movie, physical breaches still occur, and are a very real security threat.
In a physical breach, the malicious actor leverages human interaction, posing as a legitimate representative of a known and trusted organisation, and uses this trust to acquire sensitive information or unauthorised areas of a business. They may use the extremely unsophisticated tailgating technique, where they follow closely behind their target, their target closely, piggybacking off their security details to gain access to a building, or even just act as other office workers, and ask the target to hold the door open for them.
The Mind Game: Understanding the Psychology Behind Social Engineering
Social engineering attacks are designed to prey on base human emotions. Whether it’s an urgent-sounding text, an amazing offer on social media, or an email from your bank saying your account has been compromised, these all work to heighten emotions and act irrationally.
And while they often prey on fear, they also use curiosity, excitement, guilt, or anger to persuade the target to open a phishing email or click a specific link to malicious websites.
Social engineering attacks are typically urgent, using perceived short timeframes to further push the target to attend to a seemingly serious problem or wonderful opportunity. A split-second decision is all it takes to act quickly—yet thoughtlessly.
But the biggest psychological danger of social engineering attacks is how they prey on trust. Receiving communication from an apparent trusted source, they arrive at the target with legitimacy, making them all the harder to ignore.
The Ripple Effect: Consequences of Social Engineering Attacks
In their effects, social engineering attacks are much like any other cyberattack. They’re designed to cause informational or financial loss, providing cybercriminals with access to damaging confidential information, or defrauding the target out of thousands or millions of dollars in ransom.
But following the incident, they have a big impact on business productivity. With the right details, cybercriminals can effectively neutralise specific business systems, or delete swathes of data, which bring business’ operations to a grinding halt.
Then there’s the cleanup, time spent rebuilding systems, databases, and entire networks, and following up with an investigation into how the attack occurred.
It doesn’t end there. Social engineering attacks are potentially more damaging to businesses than more sophisticated cyberattacks. It’s because of the human element: if a business can’t trust its people to do the right thing, how can their stakeholders?
It damages their faith in the company, causing them to lose clientele, lose business, and potentially even damaging stock prices; effects that all take some time to recover from.
Who Bears the Brunt of Social Engineering Attacks?
In business, cybercriminals tend to target both high-value and low level employees alike.
CEOs and CFOs are targeted for their knowledge and control of a company, and access to extremely secure areas, or they’re defrauded to achieve significant monetary gain.
Low level employees, just doing their jobs, are targeted in ways that can potentially compromise larger parts of their business, such as paying an invoice, re-entering business credit card details, on a spoofed link, or providing the details of further victims to target.
But social engineering attacks also exploit the vulnerable. In the 2022 period, Scamwatch, ReportCyber, the Australian Financial Crimes Exchange, IDCARE, the Australian Securities and Investment Commission, and other government agencies received a combined total of over 500,000 reports of scams, both online and offline. Reporting shows that older Australians were increasingly the targets of social engineering attacks, losing more money than any other age group, with combined losses of $120.7 million.
What a Social Engineering Attack Looks Like
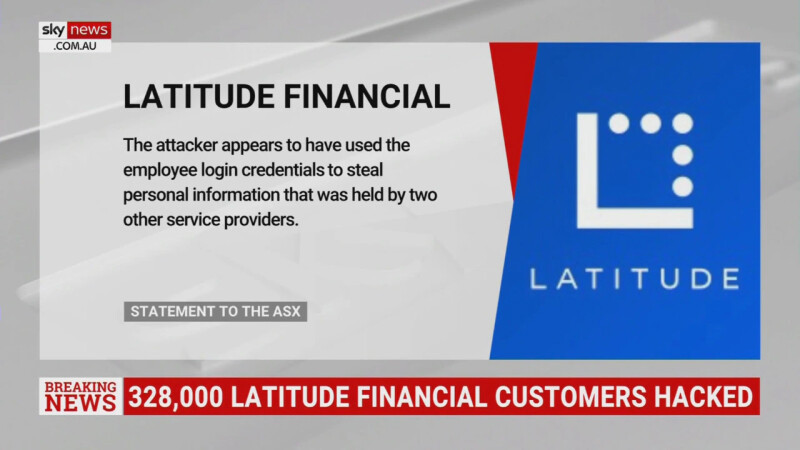
One of the most prominent examples in recent news is the Latitude Financial Services data breach on 15 March 2023.
Bearing all the hallmarks of a social engineering attack, the attack originated from a major Latitude vendor, where hackers breached the system by obtaining Latitude employee credentials, stealing the details of up to 7.9 million drivers licences and 53,000 passport numbers.
But the largest Australian data breach of its kind to date is the October 2022 Medibank data breach. Details of 9.7 million Medibank customers were stolen by hackers and shared online, with the perpetrators demanding a $15 million ransom.
Again, the breach occurred by a malicious actor securing the login credentials of a Medibank employee with privileged system access, demonstrating all the signs of a successful phishing attack. Medibank is now facing a class-action lawsuit from the victims of the breach.
Proactive Defence: Prevention Strategies Against Social Engineering Attacks
When it comes to building your Human Firewall, there are both technical and common-sense solutions you can deploy to proactively identify and avoid falling victim to social engineering attacks.
Discuss good IT security protocol with your staff
The first step to being prepared is being aware. Provide your teams with the necessary understanding and training so they know what to do in the event of a potential social engineering attack. Instil that it’s better to be overprepared and make a proactive safety call rather than risk an attack, and demonstrate that they have your trust and support to act in your company’s best interest.
By creating a risk-aware culture, and giving them the skills, training, and support to see it through, then your people will feel completely comfortable in reporting any incidents, no matter how mundane they might seem.
Email and SMS security awareness training
Acting with caution is crucial in preventing social engineering attacks. So make sure your people apply regular training into good email and SMS practice.
It’s as simple as never clicking on links from unknown sources, or manually typing in a URL into the browser address bar instead. Or bypassing the malicious link altogether, and going directly to the reported sender’s website to find a legitimate link for the action in question.
Only open emails from trusted sources
Ensure that your people don’t open emails from unknown senders. If they have unknown sources arrive in their inbox, double-check the sending entity. Do a quick email search, company check, and touch base with the rest of their team to identify why this individual might be contacting them. And even then, be careful about what they open: email addresses can be easily spoofed.
Multi factor authentication
Multifactor authentication (MFA) is a strong step that can prevent social engineering attacks. There are many MFA solutions out there that send a notification directly to your smartphone, providing an easy confirmation of any login attempts to your accounts.
Use common sense
Simple common sense goes a big way towards avoiding social engineering attacks.
- Your people should know that if an offer or notification sounds too good to be true, it probably is. Don’t open the email, or click the link.
- Be wary of any unsolicited friendship requests on social media platforms, too, and stay alert for any red flags of trying to build and abuse trust.
- Don’t leave devices unsecured in public places.
- And definitely don’t plug an unknown USB into their computer.
Ensure firewall and antivirus software is updated
Ensuring your company has a strong anti virus software and firewall provides the first layer of support against social engineering attacks. But make sure you keep them updated, and ensure automatic updates are turned on. Missing an update can open you up to vulnerabilities you may not even be aware of.
Test IT resilience
IT penetration testing tests your cyber resilience, but you can also run tests to check your people’s awareness of social engineering attacks. You can try engaging your IT team, or an external organisation, to simulate a phishing attack, use baiting tactics, or run pretexting scenarios against your people and see how they respond.
A professional cyber security team can work with you to implement a robust cyber security plan that provides the right training, support, and guidance to ensure your people know how to identify and avoid social engineering attacks
React, Recover, Reform: Responding to Social Engineering Attacks
One of the big problems with social engineering attacks is that they often go unreported. Staff clicking on a suspect link or divulging information on malicious sites can feel a great sense of shame.
Notify your security team
If one of your team receives spear phishing emails or a fraudulent text urgently requesting sensitive information or a similar activity, the first step to responding to social engineering attacks is to notify your IT team or cyber security partner.
Your cyber security partners will have protocol in place for what to do if your company is compromised, and they’ll typically have proactive security scanning in place to ensure external threats are neutralised before becoming an issue. But without notification, a social engineering attack might not be immediately obvious, so the first step in responding to an attack is notifying your cyber security team.
Also, ensure you have robust policies in place stating what to do in the instance of these attacks, so your people know the process to follow and feel supported in making the right call.
Report the incident
The next step is to make an incident report. Create a clear report that includes:
- Name of the target
- Time and date of the attack
- Description of the attack, which includes the attack vector, nature of the attack, the actions taken by the target, and the details they supplied
- Outcome of the attack
- Any effects following
Then provide this to your IT or cyber security team as soon as possible. Reporting incidents allows you to potentially identify patterns and learn from these attacks. It also helps you work with the victim to help them understand what they did right, their security mistakes, and how to avoid future attacks.
Recovery
Your cyber security team can identify and assess what happened, then work to contain the damage.
They’ll immediately ringfence any compromised operating systems, or devices, and ensure your data is backed up and secure. They’ll restore files from your backups, and then help you change all passwords and user credentials.
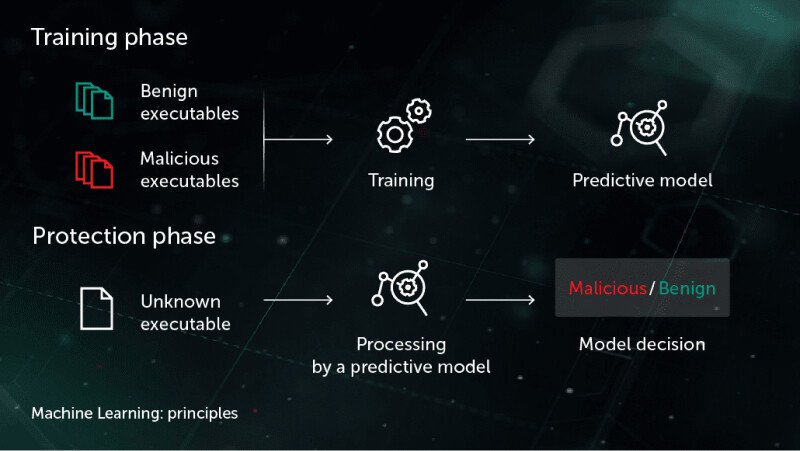
Levelling Up: Emerging Technologies to Combat Social Engineering
Emerging cyber security technologies, particularly AI and Machine Learning (ML), are playing an increasingly significant role in the battle against social engineering attacks.
These innovative technologies harness their computational power and learning capabilities to detect, predict and counteract such attacks. AI and ML algorithms analyse vast amounts of data to discern patterns associated with typical social engineering tactics, such as phishing emails or fraudulent calls. They facilitate real-time identification of these threats and offer a proactive approach to security by flagging or quarantining suspicious activity before it can inflict damage.
Incorporating cyber behavioural analytics into this technology further enhances its efficacy. This technique allows systems to understand normal user behaviour and identify anomalies that could indicate a social engineering attack.
By scrutinising online behaviour, communication patterns and data access habits, these tools develop a baseline of “normal” activity for each user. Subsequently, any deviation from this norm, such as an unusual email request or unexpected system access, triggers an alert. This approach is highly effective against social engineering since these attacks often involve atypical actions or requests.
These technologies, however, are not silver bullets. As AI and behavioural analytics become more sophisticated, so too do the tactics employed by cybercriminals. It’s a perpetual game of cat and mouse, but the advent of these technologies certainly tilts the scale in favour of defence, providing an extra layer of protection against the persistent and evolving threat of social engineering.
Create a Robust Human Firewall With TechBrain
It’s crucial to partner with a cyber security team that understands your needs, and supports your people to build a strong human firewall.
At Techbrain, we work with you to create tailored cyber security strategies to ensure your people know how to stay safe online, and help you put clear and actionable plans in place to get your business back up and running faster in the event of any network compromise.
Contact us today to discuss a free security consultation, and see how we can help you create a more secure cyber security posture.