In this article
In a world where cyber threats are getting more sophisticated and widespread, threatening business processes and reputations, having an understanding of current cyber security standards is not just a technical requirement but a business imperative.
But where to start? In a complex and ever-changing field, the Australian Government gives local businesses a framework for compliance with essential cyber security standards, developed by the Australian Signals Directorate (ASD) – the Essential 8 Maturity Model.
It’s not a set of guidelines, it’s a cyber security approach, a layered defence mechanism that’s critical to your information assets. In a proactive and practical approach to digital security that’s always up-to-date, addressing the evolving nature of cyber risks (see ASD 2023 cyber threat report) in a structured way.
We can’t stress enough the importance of staying current with the ASD’s latest guidance to keep your business safe, so let’s dive into the Essential 8 Maturity Model and understand its role as a guide to improving and maintaining your organisation’s cyber security posture.
What is the ASD Essential 8
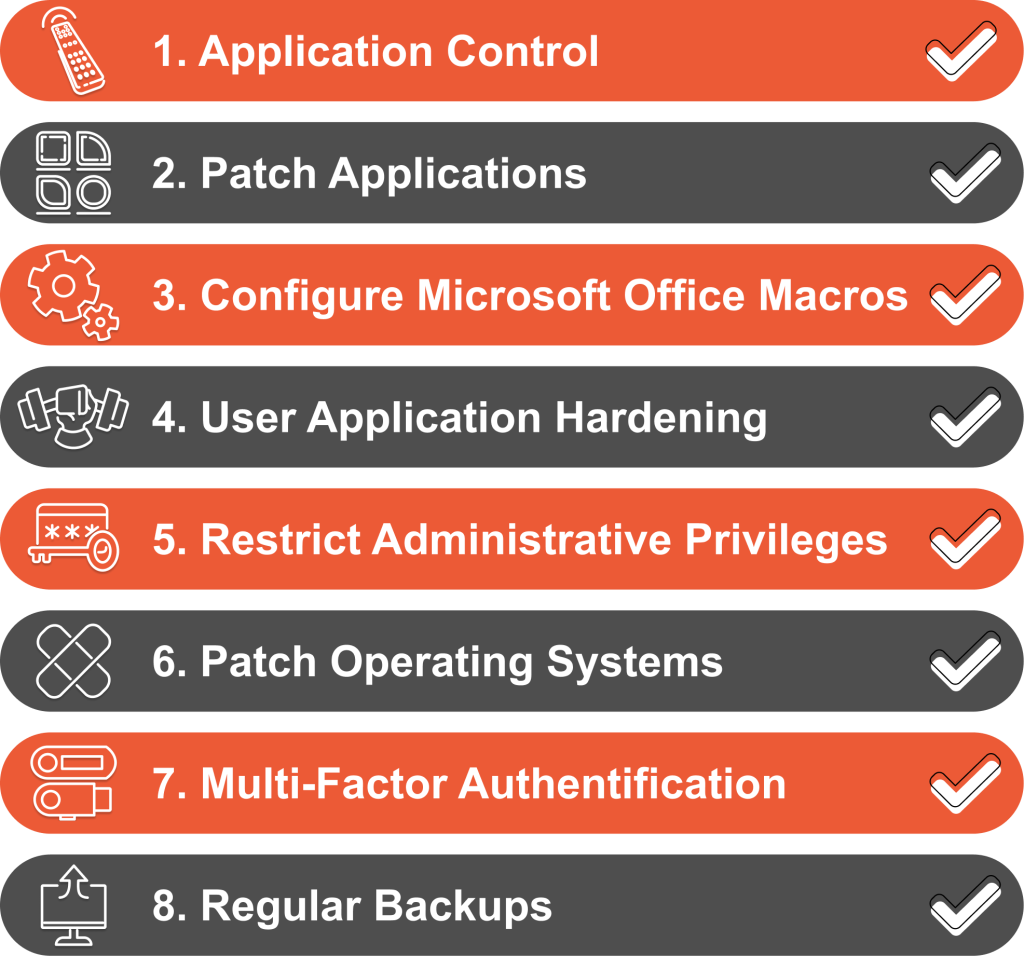
The ASD Essential 8 are 8 mitigation strategies that are the foundation of good cyber defence. Understanding these strategies is essential for any organisation looking to strengthen its cyber security.
Application Control
Application control is a key security control that involves controlling executable software within your network. This means only approved and verified applications are allowed to run, so malicious software can’t get in. It’s achieved through whitelisting or blacklisting of software libraries and rigorous application integrity evaluation.
Patching Applications
Microsoft Office Macros must be managed with care. The only mitigation strategy here is to restrict macro usage to essential and trusted instances only, so minimising the risk of macro enabled malware. Strict policy and user education on safe use of macros are key.
User Application Hardening
User application hardening reduces the attack surface of software applications. This means configuring settings within web browsers and other applications to disable unnecessary features that can be used by attackers. Techniques include disabling unneeded plugins, scripting functionality and using security focused browser settings.
Restricting Administrative Privileges
This strategy means limiting the number of users with administrative privileges within an organisation. By reducing the pool of privileged users with high level access rights the risk of exploitation is reduced. This means rigorous access control management, regular reviews of user privileges and application of the principle of least privilege.
Patching Operating Systems
Structured approach to updating and securing operating systems by addressing identified vulnerabilities. A full patch patch management process is key to ensuring security controls the timely and effective deployment of security patches. Continuous monitoring for new vulnerabilities and updates is also critical so you can keep your operating system up to date and secure against emerging threats.
Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring multiple forms of verification when accessing systems. This reduces the chance of unauthorised access as it combines something you know (like a password) with something you have (like a mobile device) or something you are (like a fingerprint).
Regular Backups
Regularly backing up data is a critical strategy for information resilience. In the event of a cyber incident, having up to date backups allows for rapid restoration of lost or compromised data. A full backup strategy should include regular backup scheduling, secure storage of backup data and regular testing of backup integrity.
Each of these strategies is part of a comprehensive cyber security plan.
They are not individual actions but interconnected parts of a holistic approach to digital security. Implementing the Essential 8 is not just about ticking boxes; it’s about creating a security culture within your organisation where every layer of defence works together.
Exploring the Maturity Model
The ASD Essential 8 Maturity Model categorises an organisation’s cyber security posture into four levels. Understanding and defining the key requirements of each level is critical for organisations to assess and improve their cyber security maturity.
Maturity Level Zero
At this level you have significant gaps in your cyber security defences.
Key requirements:
- No implementation of the Essential 8 strategies.
- No regular reviews or updates to your cyber security practices.
- No awareness or training among staff for cyber security.
This level means you need to take immediate action to put in place basic cyber security measures.
Maturity Level One:
Represents basic cyber security practices.
Key requirements:
- Some of the Essential 8 strategies implemented.
- Basic cyber security policies and procedures.
- Some staff training and awareness on cyber security.
This level shows cyber security is important but needs more development and implementation.
Maturity Level Two:
Indicates a more advanced and proactive cyber security stance.
Key requirements:
- Implementation of most, if not all, of the Essential 8 strategies.
- Regular review and updates of cyber security measures.
- Staff training and incident response plans.
- Integration of cyber security into the organisational culture and regular operations.
Organisations at this level are actively managing and updating their cyber security defences.
Maturity Level Three:
Represents the highest level of cyber security maturity.
Key requirements:
- All Essential 8 strategies implemented.
- Continuous monitoring and proactive threat assessment.
- Advanced staff training, including simulation exercises and continuous learning.
- Strong governance, including board-level engagement and regular reporting on cyber security posture.
- Ability to quickly adapt and respond to emerging threats and technologies.
This level means the business is not just protecting against current threats but future threats.
Each level builds on the previous one, from reactive to proactive to advanced cyber security. The goal is to strive for Maturity Level Three where cyber security is part of the business culture and mindset.
Overview of Recent Changes to the Essential 8
The Australian Signals Directorate (ASD) updated the Essential Eight Maturity Model in November 2023. These changes reflect evolving cyber security threats and aim to strengthen organisational defences.
Patch Applications and Operating Systems
Prioritised Patching: Critical vulnerabilities (e.g., facilitating privileged access or remote code execution) must be patched within 48 hours.
Application Patching Timeframes: Applications interacting with untrusted internet content now need to be patched within 2 weeks, with weekly vulnerability scanning.
Balancing Patching for Operating Systems: Less critical devices (e.g. non-internet facing servers) have extended patching timelines from 2 weeks to 1 month.
Drivers and Firmware: Maturity Level Three now includes patching for drivers and firmware vulnerabilities.
Multi-factor Authentication (MFA)
New MFA Standards: Maturity Level One now requires MFA to include ‘something users have’ and ‘something users know’.
Phishing-Resistant MFA: More focus on phishing-resistant MFA options especially for online services that store sensitive data.
MFA for Workstations: MFA for workstation access required at Maturity Levels Two and Three.
Limit Administrative Privileges
Governance Processes: Improved processes for granting, controlling and revoking privileged account access.
Internet Access for Privileged Accounts: Controlled and limited internet access for these accounts.
Hardening Administrative Infrastructure: Maturity Level Three includes Secure Admin Workstations and Windows security features.
Application Control
Annual Review of Control Rulesets: Review and implement Microsoft’s recommended application blocklists every year at Maturity Level Two.
Disable Microsoft Office Macros
Remove Macro Execution Event Logging: Not recommended as it provides limited benefits and is hard to implement.
Enforce Secure Macro Signatures: V3 digital signatures required at Maturity Level Three.
User Application Hardening
Disable Unsupported Software: Disable or uninstall Internet Explorer 11.
PowerShell Logging: Native PowerShell logging, including command line process creation events.
Regular Backups
Prioritise Backups: Prioritise based on business criticality.
How to Measure Your Current Cyber Security Against the Model
To align with the ASD Essential 8 Maturity Model you need to measure your current cyber security and implement changes in a structured way.
Here’s a high-level guide to get you started.
Initial Cyber Security Measurement
Understand the Essential 8: Get a deep understanding of the ASD Essential 8 strategies and maturity levels.
Current State: Measure your current cyber security against each of the Essential 8 strategies. This includes what you have in place and how it aligns to the model.
Vulnerability and Gap Analysis: Identify where you are not meeting the model. This includes vulnerabilities in your systems, processes and policies.
Risk Assessment
Assess Cyber Security Risks: Understand the impact of the identified vulnerabilities and gaps. Determine the likelihood of these risks occurring and the impact on your business.Prioritise: Based on the assessment, prioritise what needs to be done first.
Measure Against the Model
Maturity Level: Determine your business’s target maturity level for each of the Essential 8 strategies. This will help you understand the gap to the target maturity level.
Take Your Cyber Security to the Next Level
Implementing the ASD Essential 8 Maturity Model is a must for any business owner in today’s cyber threat landscape. It’s more than a tick box exercise; it’s a framework to de-risk your business against cyber threats. Each of the eight strategies, from application control to regular backups, is a layer of defence for your business’s sensitive data and reputation.
As you move through the maturity levels from zero to three you’re not just improving your cyber security, you’re building a digital resilience culture for your business. Cyber security is a marathon not a sprint. Regularly updating your strategies to counter new threats is key. By committing to cyber security you’re not only protecting your business assets but also customer trust and your business’s reputation.
Being Essential 8 compliant means you value and prioritise your business’s security and longevity in today’s business world.
Want to get your cyber maturity level up to speed? Contact the TechBrain team.