In this article
In the digital age, the battleground for security has expanded far beyond the physical realm into the very psyche of individuals and organisations. Social engineering attacks epitomise this shift, exploiting not the weaknesses in software, but in human psychology and social behaviour.
Instead of breaking into systems through technical hacks, these cyber criminals tap into our very human vulnerabilities, our routines, the trust we place in others and our social behaviours. They’re masters at manipulating their targets into accidentally revealing sensitive information or taking actions that swing wide the gates that secure our digital fortresses.
A Journey Into The Cybercriminal Mind
Diving into the mindset of cybercriminals opens up a world where exploiting human psychology is as critical as hacking skills. This deep dive into human hacking shows us a space where manipulation becomes an art and understanding the human psyche is as important as mastering code. Cybercriminals meticulously orchestrate scenarios that feel incredibly real, tapping into our deepest fears, betraying our trust and sparking our curiosity to meet their goals.
We’ll highlight the importance of a comprehensive security strategy that goes beyond tech solutions to also include educating staff about the mind games played in social engineering attacks; to fortify our digital defences by protecting not just our data, but also our decision-making processes from being compromised.
Unpacking Social Engineering
Definition of Social Engineering
In the cyber security landscape, “social engineering” has become a term for a specific kind of security breach that focuses on human psychology rather than technological vulnerabilities.
This strategy manipulates individuals into giving up confidential information or taking actions that breach their own security.
Differing from the direct hacking of systems, social engineering plays the long game, exploiting the natural human tendencies of trust and social interaction. It’s essentially the digital era’s con artistry, leveraging the immense value of information in our interconnected world.
A Brief History & Evolution of Social Engineering Attacks
The evolution of social engineering tactics within the cyber landscape has mirrored the swift progress of technology. Initially, tactics like phishing, broadly targeting a wide audience with deceptive emails kicked off the journey of social engineering in cybersecurity. These emails were crafted to look as if they were sent from well-known entities, tricking people into exposing their personal information.
As the digital era entrenched itself into our daily lives, the art and science of social engineering attacks grew in complexity. Cyber adversaries moved beyond the basic phishing schemes to develop more sophisticated and strategic methods. These evolved tactics were designed to be more targeted and personalised, utilising the wealth of personal data available online to increase their success rates.
This shift from wide-net approaches to strategies that are both psychologically and technically refined underscores a significant development in the realm of social engineering techniques.
Modern day cybercriminals no longer rely solely on chance; they now employ detailed research and cunning psychological ploys to achieve their aims, marking a profound evolution in the execution of social engineering in the age of the internet.
Why Social Engineering is Thriving
In today’s digital-first world, where almost every piece of our lives can be found online, the opportunities for social engineers have exploded.
The massive amounts of personal information on social media, combined with the increasing sophistication of cybercriminals, have made social engineering a critical threat. It exploits the weakest link in any security system, the people using it. As we’ve moved more of our lives, finances and work online. The potential rewards for successful social engineering attacks have equally grown, making social engineering an attractive and lucrative scheme for cybercriminals.
Social engineering thrives on the overload of information and the pace of communication in the modern world. With so much to process, individuals and organisations can easily overlook the subtleties that might reveal a scam. Moreover, the trust we place in digital communication. from emails to instant messages creates the perfect breeding ground for these attacks.
Educating individuals and organisations about these tactics is more than a preventative measure; it’s become paramount to a comprehensive security strategy.
The Profile of a Social Engineer
Social engineers are the chameleons of the cyber world, blending psychological savvy with technical skills to manipulate human behaviour. Their success hinges not just on what they know, but on how well they can play the role expected of them in any given scenario.
Traits Common Among Social Engineers
Empathy
Ironically, a social engineer’s ability to empathise with others is what allows them to exploit the emotions of their targets effectively.
Resourcefulness
They are adept at using whatever information and tools are at their disposal, often turning seemingly benign data into powerful leverage.
Charisma
A persuasive and likeable demeanour helps social engineers to lower the defences of their targets, making it easier to extract information or influence actions.
Observation
Keen observational skills allow them to pick up on subtle cues that can be used to tailor their approach to each unique target.
Patience
Social engineering often requires nurturing a false sense of security over time, meaning patience is key to their deceptive practices.
Skills That Set Them Apart
Advanced Research
Social engineers excel in gathering detailed background information on their targets to make their attacks more personalised and convincing.
Psychological Manipulation
An understanding of human psychology and common behavioural responses enables them to craft scenarios that are more likely to show human error and elicit the desired outcome.
Technical Proficiency
While their methods are heavily based on social manipulation, a robust understanding of technology and cybersecurity helps them identify and exploit technical vulnerabilities as part of their strategy.
Communication
Exceptional verbal and written communication skills are crucial, enabling them to convincingly assume various identities or roles.
The Anatomy of a Social Engineering Attack
A social engineering attack unfolds through a series of calculated steps, each designed to exploit trust and manipulate human emotions to breach security measures. Understanding this anatomy is essential to recognizing and mitigating potential threats before they can cause harm.
Research and Information Gathering
The initial phase involves extensive research to collect as much personal and organisational information as possible. Social engineers scour public databases, social media profiles, company websites and even dumpster dive to gather sensitive details. This phase is crucial for tailoring the attack to the target’s specific vulnerabilities.
Target Identification
Identifying the individuals or roles within an organisation that have access to the desired information or systems.
Data Collection
Compiling detailed profiles on targets, including their social habits, professional connections, personal interests and security habits.
Planning and Strategy Development
With a wealth of information at their disposal, attackers develop a strategy that outlines how they will engage with the target. This plan includes selecting the most effective type of attack (phishing, pretexting, baiting, etc.), crafting the message or scenario and deciding on the communication channel (email, phone, in-person).
Choosing the Attack Vector
Determining the most suitable social engineering technique based on the target’s vulnerabilities and the attacker’s goals.
Crafting the Narrative
Creating a believable story or pretext that will be used to engage the target, leveraging the collected information to increase authenticity.
Establishing Contact
The next step is to initiate contact with the target, often under the guise of a trusted entity or individual. The method of contact is carefully chosen based on the target’s preferences and habits, ensuring the highest likelihood of engagement.
Engagement
Using personalised communication tailored with specific details gathered during the research phase to make the request or proposition seem legitimate.
Manipulation Tactics
Employing psychological principles such as urgency, authority, scarcity and social proof to persuade the target to act.
Execution
This is the critical moment where the social engineer attempts to deceive the target into divulging confidential information, clicking on a malicious link, transferring funds or performing some other action that serves the attacker’s objectives.
Request for Action
Convincing the target to take the desired action, which directly compromises security or provides further access to sensitive information.
Exploiting Trust
Leveraging the established rapport and the illusion of legitimacy to overcome any lingering doubts the target may have.
Extraction and Exploitation
Once the target has taken the bait, the attacker extracts the valuable information or achieves their desired outcome. This may involve stealing credentials, infecting systems with malware or obtaining confidential documents.
Data Harvesting
Collecting the compromised information or access gained through the attack.
Lateral Movement
Using the initial compromise to further penetrate the organisation’s network or systems, often aiming for more significant exploits.
Concealment
To prolong their access and avoid detection, social engineers often take steps to erase any signs of their activities. This can involve deleting logs, disguising malware activities or manipulating victims into believing their actions were legitimate.
Misdirection
Creating plausible explanations for any anomalies that might raise suspicions about the attack.
Continued Manipulation
Maintaining control over the target or using the compromised information to launch additional attacks before exiting the scenario.
Common Attack Vectors
Below is a brief summary of some of the most commonplace types of social engineering.
Phishing
This widespread method involves sending fraudulent emails that mimic legitimate communications from trusted entities to trick recipients into divulging sensitive information, such as login credentials or credit card numbers.
Spear Phishing
A more targeted version of phishing, spear phishing focuses on specific individuals or organisations. These emails are highly personalised, often using information gathered from social media or other sources to appear more credible.
Vishing (Voice Phishing)
Vishing uses phone calls to deceive people into providing personal information or financial details. Attackers often pose as bank officials, tech support, or government agents to create a sense of urgency or authority.
Smishing (SMS Phishing)
Similar to phishing, smishing involves sending text messages that lure individuals into clicking malicious links or providing personal information under false pretences, such as a problem with their bank account or a prize they’ve won.
Pretexting
Involves creating an imaginary scenario to attain access to secure information. They might impersonate co-workers, police, bank officials, or other persons with right-to-know authority to justify their inquiries.
Baiting
Baiting involves offering something enticing to the target, such as free software downloads, in exchange for information or access. The “bait” often contains malware or leads the victim to compromised websites.
Quid Pro Quo
Similar to baiting, quid pro quo offers a benefit in exchange for information. This might involve an attacker offering free IT assistance in exchange for login credentials or other sensitive data.
Tailgating or Piggybacking
Tailgating, also known as piggybacking, is a physical security breach where an unauthorised individual gains access to a restricted area or system by closely following an authorised person without their knowledge. This tactic exploits social norms and politeness, such as asking someone to hold the door open under the pretence of forgetting their access card.
Business Email Compromise (BEC)
In BEC attacks, cybercriminals impersonate executives or high-level employees to trick employees into transferring money or sensitive information. This often involves urgent requests for wire transfers or payment to fraudulent accounts.
Watering Hole Attacks
Attackers compromise a popular website known to be visited by their target group and infect it with malware. The goal is to infect a visitor’s device and gain access to the network of the targeted organisation.
Honey Trap
This method involves creating a fake persona to form a relationship with the target. The attacker then exploits this relationship to extract confidential information or gain access to systems.
Scareware
Victims are bombarded with false alarms and fictitious threats, urging them to install software that supposedly fixes a critical security issue but is actually malware.
CEO Fraud
Attackers impersonate the CEO or another high-ranking executive in an organisation to deceive employees, usually in the finance department, into executing unauthorised wire transfers or sending out confidential information.
Each of these vectors leverages a different aspect of human nature, such as trust, fear, curiosity, or the desire to be helpful, demonstrating the varied and creative approaches cybercriminals use to exploit their targets. Awareness and education are key to defending against these types of attacks.
Case Studies:
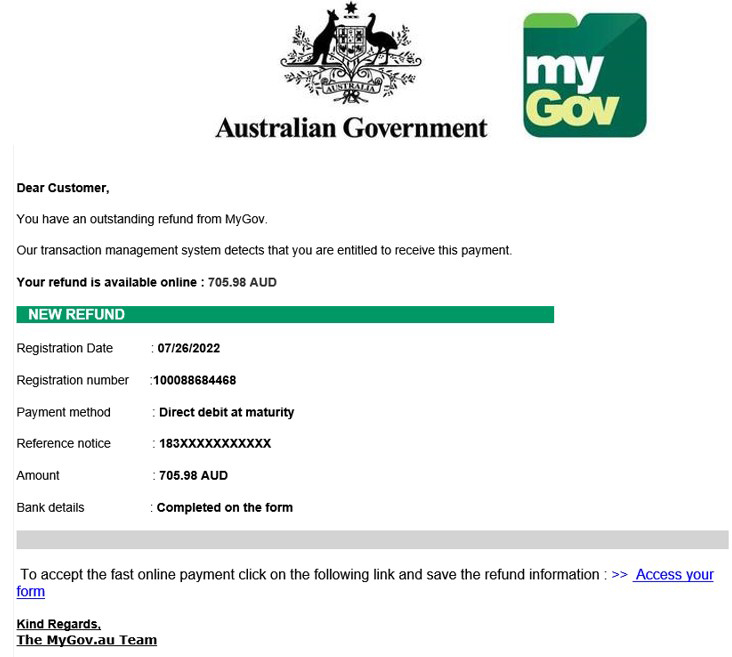
MyGov Scam (2023)
A significant scam operation targeting MyGov users was uncovered in 2023, involving “scam-in-a-box” kits sold on the dark web. These kits enabled criminals to create fake websites and launch sophisticated phishing attacks on Centrelink, the Australian Tax Office (ATO), and Medicare accounts.
Over 4,500 MyGov scams have been confirmed, leading to the suspension of thousands of accounts each month due to suspected fraud. The kits provided criminals with the tools to run multiple scams simultaneously and evade detection, with some even redirecting more tech-savvy users to the official MyGov site to avoid suspicion.
NAB (National Australia Bank) Phishing Scam (2017)
In 2017, a sophisticated phishing scam targeted National Australia Bank (NAB) customers, circulating emails that falsely informed recipients their accounts had been disabled. The scam email, which had the subject line ‘Notification’ and was sent from [email protected], directed users to “click here” to reactivate their accounts. This link led to a realistic copy of the NAB internet banking website, designed to harvest victims’ account IDs and passwords.
Security provider MailGuard intercepted thousands of these phishing emails on the afternoon of May 25, highlighting the scam’s widespread impact. The fake NAB website created by the scammers was a key tool in their attempt to collect banking details for financial gain, using the information to make unauthorised transactions.
NAB responded quickly to the scam, advising customers to forward suspicious emails to [email protected] for investigation and then delete them, as part of their effort to protect customers from fraudulent activities.
Woolworths Rewards Points Scam (2021)
Woolworths shoppers experienced significant losses due to a hacking scam targeting their Everyday Rewards accounts. Scammers drained hundreds of dollars in rewards points, with one customer reporting a loss of $250 saved for Christmas shopping. The fraudsters accessed accounts using valid login details, leading to suspicions that they obtained these credentials through online scams or other illicit means.
Woolworths responded by assisting affected members, emphasising the importance of strong, unique passwords and vigilance against scams. Despite no evidence of a breach in Woolworths’ IT systems, the incidents highlighted the sophisticated methods used by hackers, including bypassing two-factor verification.
Customers impacted by the scam were promised the reinstatement of their points, though some faced delays in resolution. This scam serves as a reminder for consumers to secure their online accounts and remain alert to potential fraud.
ANU Data Breach (2018)
The Australian National University (ANU) experienced a significant data breach in late 2018, which was discovered in May 2019 and publicly disclosed in June. This breach saw hackers gaining access to up to 19 years’ worth of data within the university’s Enterprise Systems Domain (ESD), encompassing human resources, financial management, student administration, and enterprise e-forms systems.
The incident report released by ANU has been praised for its transparency, detailing the sophisticated methods employed by the attackers, including spear phishing campaigns, custom malware and exceptional operational security that left few traces.
The attackers were noted for their precision and ability to evade detection systems, evolving their techniques throughout the campaign. They managed to exfiltrate less data than initially feared but left ANU with no clear understanding of the full extent of the stolen data or the attackers’ motives.
In response, ANU has implemented safeguards to prevent similar breaches, emphasising the importance of strong, unique passwords and vigilance against scams. This breach serves as a stark reminder of the sophisticated threats facing educational institutions and the need for robust cybersecurity measures.
Prevention and Protection Strategies
In today’s digital landscape, safeguarding personal and sensitive information requires a proactive approach. Implementing effective prevention and protection strategies can significantly reduce the risk of falling victim to social engineering attacks.
Safe Communication and Account Management Habits
Verification of Sources
Always verify the authenticity of communication before responding or clicking on any links. Be cautious of unsolicited emails, messages, or phone calls requesting personal information or urgent action.
Use Official Channels
When managing online accounts, access them directly through official websites or trusted applications rather than clicking on links provided in emails or messages.
Strong Passwords
Use unique, complex passwords for each online account and consider using a reputable password manager to securely store and manage passwords.
Enable Two-Factor Authentication (2FA): Enhance the security of accounts by enabling 2FA wherever possible, adding an extra layer of protection beyond passwords.
Safe Network Use Habits
Secure Wi-Fi Networks
Ensure that home and workplace Wi-Fi networks are password-protected and use encryption protocols such as WPA2 or WPA3 to prevent unauthorised access.
Avoid Public Wi-Fi
Exercise caution when using public Wi-Fi networks, as they are often insecure and susceptible to interception by cybercriminals. Consider using a virtual private network (VPN) for added security when connecting to public Wi-Fi.
Regular Updates
Keep devices, software, and applications up to date with the latest security patches and updates to protect against known vulnerabilities.
Spam Filters
Implement spam filters on email accounts to automatically detect and filter out suspicious or unsolicited emails, reducing the likelihood of falling victim to phishing attempts and malicious content.
Safe Device Use Habits
Antivirus Software
Install reputable antivirus and anti-malware software on all devices, including computers, smartphones, and tablets, and keep them updated regularly.
Firewall Protection
Enable built-in firewalls on devices and consider using additional firewall software for added protection against unauthorised access.
Be Wary of Links and Attachments
Exercise caution when clicking on links or downloading attachments from unknown or untrusted sources, as they may contain malware or phishing attempts.
By adopting these safe communication, network use and device use habits, individuals and organisations can strengthen their defences against social engineering attacks and minimise the risk of falling victim to cybercrime. Vigilance, awareness and proactive security measures are key to staying one step ahead of cyber threats in an increasingly interconnected digital world.
Conclusion
Understanding the tactics and psychology behind social engineering attacks is essential for safeguarding against cyber threats in today’s digital age. We’ve explored how cybercriminals exploit human vulnerabilities through manipulation and deception, highlighting the importance of staying vigilant and informed.
As we’ve seen, social engineers prey on trust, curiosity and fear to trick individuals and organisations into divulging sensitive information or performing risky actions. By recognising these tactics and implementing proactive security measures we can mitigate the risk of falling victim to these insidious attacks.
However, the fight against social engineering doesn’t end here. It requires ongoing vigilance and education to stay ahead of evolving threats. We must remain proactive in updating our security practices, educating ourselves and others about the latest scams and fostering a culture of cybersecurity awareness.
Together, we can build a more resilient digital ecosystem and protect ourselves against the tactics of social engineers.