In this article
In today’s digital landscape, much of security plays out in our heads as much as on our networks. Social engineering embodies that shift. It targets behaviour and judgment, not just software flaws, by leaning on psychology and everyday habits.
Rather than breaking code, attackers probe routines, trust and social cues. They coax people into sharing sensitive details or taking small actions that unlock bigger problems for an organisation.
A journey into the cybercriminal mind
To understand social engineering, you need to see how attackers think. Technical skill matters, but so does an intuition for people. The most effective campaigns feel ordinary and urgent at the same time. They exploit fear, curiosity and authority to slip past our defences and steer decisions.
This is why a strong security program must reach beyond tools. Training that explains the tricks and pressure tactics helps staff pause, verify and choose safer options in the moment. The goal is to protect both data and the decision-making that guards it.
Unpacking social engineering
Definition
In cyber security, social engineering refers to attacks that misuse human behaviour rather than technical weaknesses. The aim is to convince someone to reveal confidential information or perform an action that weakens their own security.
Unlike direct system hacking, social engineering often unfolds over time. It blends credibility, rapport and timing to turn ordinary interactions into opportunities. In short, it is modern confidence fraud adapted to a connected world.
A Brief History into the Evolution of Social Engineering Attacks
The evolution of social engineering tactics in the cyber world has mirrored the rapid pace of technology. Phishing, targeting a wide audience with deceptive emails, was the first social engineering attack. These emails were designed to look like they came from well-known entities, getting people to reveal their personal information.
As the digital world became part of our daily lives, the art and science of social engineering attacks got more complex. Cyber adversaries moved beyond the basic phishing to more sophisticated and strategic methods. These evolved tactics were more targeted and personalised, using the wealth of personal data online to increase their success rates.
This shift from wide-net approaches to techniques that are both psychologically and technically refined is a big deal in the world of social engineering.
Modern day cybercriminals no longer rely on chance; they now use detailed research and psychological tricks to get what they want; that’s a big evolution in social engineering in the age of the internet.
Why Social Engineering is Thriving
In today’s digital-first world where almost everything about us can be found online, the opportunities for social engineers have grown exponentially.
The amount of personal information on social media combined with the sophistication of cybercriminals has made social engineering a major threat. It exploits the weakest link in any security system, the people using it. As we’ve moved more of our lives, finances and work online. The rewards for successful social engineering attacks have grown equally, making social engineering an attractive and profitable business for cybercriminals.
Social engineering thrives on the information overload and the speed of communication in the modern world. With so much to process, individuals and organisations can easily miss the subtleties that might reveal a scam. And the trust we have in digital communication from emails to instant messages creates the perfect breeding ground for these attacks.
Educating individuals and organisations about these tactics is more than a preventative measure; it’s become essential to a comprehensive security strategy.
The Profile of a Social Engineer
Social engineers are the chameleons of the cyber world, blending psychological skills with technical skills to manipulate human behaviour. Their success depends not just on what they know but on how well they can play the role expected of them in any given scenario.
Traits Common Among Social Engineers
Empathy
Ironically a social engineer’s ability to empathise with others is what allows them to exploit the emotions of their targets effectively.
Resourcefulness
They can use whatever information and tools they have at their disposal, often turning benign data into powerful leverage.
Charisma
A persuasive and likeable personality helps social engineers to lower the defences of their targets, making it easier to extract information or influence actions.
Observation
They can pick up on subtle cues to use against each target.
Patience
Social engineering often requires creating a false sense of security over time, so patience is key to their deception.
Skills That Set Them Apart
Advanced Research
Social engineers are good at gathering detailed background information on their targets to make their attacks more personal and convincing.
Psychological Manipulation
Understanding of human psychology and common behavioural responses allows them to craft scenarios that will show human error and elicit the desired outcome.
Technical Proficiency
While their methods are based on social manipulation, a good understanding of technology and cybersecurity helps them identify and exploit technical vulnerabilities as part of their strategy.
Communication
Exceptional verbal and written communication skills are essential to convincingly play different roles or identities.
The Anatomy of a Social Engineering Attack
A social engineering attack unfolds in a series of steps, each designed to exploit trust and manipulate human emotions to breach security. Knowing this anatomy is key to recognising and stopping potential threats before they can cause harm.
Research and Information Gathering
First phase is research to collect as much personal and organisational information as possible. Social engineers scour public databases, social media profiles, company websites and even dumpster dive to get sensitive info. This phase is critical to tailor the attack to the target’s specific weaknesses.
Target Identification
Identify the individuals or roles within an organisation that have access to the info or systems.
Data Collection
Build profiles on targets, including their social habits, professional connections, personal interests and security habits.
Planning and Strategy Development
With all the info gathered, attackers develop a plan that outlines how they will engage with the target. This plan includes choosing the best type of attack (phishing, pretexting, baiting, etc.), crafting the message or scenario and deciding on the communication channel (email, phone, in-person).
Choosing the Attack Vector
Decide on the best social engineering technique based on the target’s weaknesses and the attacker’s goals.
Crafting the Narrative
Create a believable story or pretext to use against the target, using the gathered info to make it more authentic.
Establish Contact
Next step is to make contact with the target, often as a trusted entity or individual. The method of contact is chosen based on the target’s preferences and habits to maximise the chance of engagement.
Engage
Use the info gathered during research to make the request or proposition personal.
Manipulation Tactics
Use psychological principles like urgency, authority, scarcity and social proof to persuade.
Act
This is where the social engineer tries to get the target to reveal confidential info, click on a link, send funds or do some other action that helps the attacker.
Ask for Action
Get the target to take the desired action that compromises security or gives more access to info.
Trust
Use the rapport and illusion of legitimacy to overcome any doubts the target may have.
Harvest and Exploit
Once the target has taken the bait, the attacker extracts the valuable info or achieves the desired outcome. This may be stealing credentials, infecting systems with malware or getting confidential documents.
Data Collection
Get the compromised info or access gained from the attack.
Lateral Movement
Use the initial breach to move laterally in the organisation’s network or systems, often for bigger exploits.
Cover
To stay in and avoid detection, social engineers may delete logs, disguise malware activity or make the victim believe their actions were legitimate.
Misdirection
Create plausible explanations for any anomalies that might raise suspicions about the attack.
Continued Control
Keep control of the target or use the compromised info to launch more attacks before exiting the scenario.
Common Attack Vectors
Here are some of the most common types of social engineering.
Phishing
Sending fake emails that look like they are from trusted sources to trick people into revealing sensitive info, such as login credentials or credit card numbers.
Spear Phishing
A more targeted version of phishing, spear phishing focuses on specific individuals or organisations. These emails are highly personalised, often using info gathered from social media or other sources to look more believable.
Vishing (Voice Phishing)
Vishing uses phone calls to trick people into revealing personal info or financial details. Attackers often pose as bank officials, tech support or government agents to create a sense of urgency or authority.
Smishing (SMS Phishing)
Like phishing, smishing involves sending text messages to trick people into clicking malicious links or revealing personal info under false pretences, such as a problem with their bank account or a prize they’ve won.
Pretexting
Creating an imaginary scenario to get access to secure info. They might impersonate co-workers, police, bank officials or other persons with right-to-know authority to justify their questions.
Baiting
Offering something to the target, such as free software downloads, in exchange for info or access. The “bait” often contains malware or leads the victim to compromised websites.
Quid Pro Quo
Like baiting, quid pro quo offers a benefit in exchange for info. This might be an attacker offering free IT support in exchange for login credentials or other sensitive data.
Tailgating or Piggybacking
Tailgating, also known as piggybacking, is a physical security breach where an unauthorised person gains access to a restricted area or system by following an authorised person without their knowledge. This exploits social norms and politeness, such as asking someone to hold the door open under the pretence of forgetting their access card.
Business Email Compromise (BEC)
In BEC attacks, cybercriminals pose as executives or high-level employees to get employees to transfer money or sensitive info. This often involves urgent requests for wire transfers or payments to fake accounts.
Watering Hole
Attackers compromise a website popular with their target group and infect it with malware. The goal is to infect a visitor’s device and get into the target organisation’s network.
Honey Pot
Create a fake persona to build a relationship with the target. Then exploit that relationship to extract confidential info or get into systems.
Scareware
Victims are bombarded with false alarms and fake threats to install software that supposedly fixes a critical security issue but is actually malware.
CEO Fraud
Attackers pose as the CEO or another high-level executive to deceive employees, usually in the finance department, into making unauthorized wire transfers or sending out confidential info.Each of these vectors targets a different human trait – trust, fear, curiosity or the desire to be helpful – showing how many ways cybercriminals attack. Awareness and education are key to defending against these types of attacks.
Case Studies:
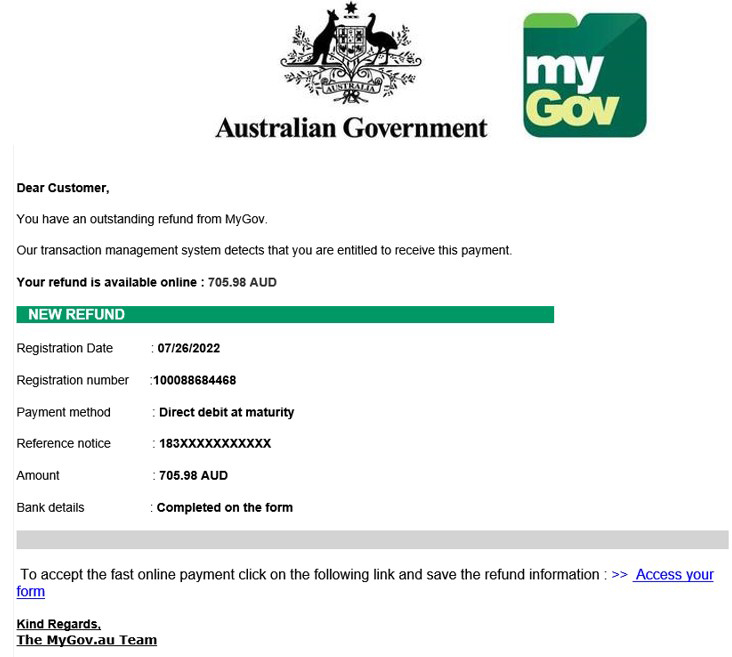
MyGov scam (2023)
In 2023 authorities found a big operation targeting MyGov users. Off-the-shelf “scam-in-a-box” kits on the dark web made it easy for crooks to spin up fake sites and run coordinated phishing campaigns against Centrelink, ATO and Medicare accounts.
Over 4,500 scam attempts were confirmed and thousands of accounts were being suspended each month on suspicion of fraud. The kits supported multiple campaigns at once and had tricks to avoid detection. In some cases if you looked too smart they would redirect you to the real MyGov site to reduce suspicion.
NAB phishing campaign (2017)
A well-crafted phishing wave hit National Australia Bank customers in 2017. Victims received an email with the subject “Notification” from [email protected] saying their accounts were disabled. A “click here” button took them to a convincing NAB Internet Banking page to capture IDs and passwords.
MailGuard reported intercepting thousands of these emails on 25 May 2017 so it was a broad reach. The fake site was used to harvest credentials for unauthorised transactions. NAB told customers to forward suspicious emails to [email protected] and then delete them, which is good advice to limit the damage.
Woolworths Everyday Rewards points theft (2021)
In 2021 scammers targeted Woolworths Everyday Rewards members and stole points. Several customers lost hundreds of dollars in value, one lost about $250 which was set aside for Christmas. The attackers logged in with valid credentials, likely gathered from other scams or sources. Some even bypassed two-factor auth.
Woolworths supported affected members and said to use strong, unique passwords and be vigilant. There was no evidence of a breach in Woolworths’ systems but it showed how effective credential reuse and social engineering can be. Most members had their points restored but some experienced delays while their cases were verified.
ANU data breach (2018)
The Australian National University had a big breach in late 2018 which was detected in May 2019 and disclosed the following month. Attackers got into the Enterprise Systems Domain and accessed HR, finance, student administration and e-forms data with records going back up to 19 years.ANU’s public report was very detailed.
It outlined a playbook that included spear phishing, custom malware and operational security that left no trace. The group changed tactics during the breach. Although exfiltration was less than initially thought, the full extent and motivation is still unknown. ANU has since tightened up and said the basics still apply: unique passwords, careful handling of emails and ongoing awareness across staff and students.
Prevention and protection strategies
Staying safe online means being deliberate about how you communicate, how you manage accounts and how you use your devices and networks. The right habits cut the odds of a successful social engineering attempt.
Safe communication and account management habits
Verify sources
Pause before you respond. Check who is contacting you, how they reached you and whether the request makes sense. Treat unexpected emails, texts or calls that ask for logins, payments or urgent action with caution.
Use official channels
If a message asks you to log in or pay a bill, go to the service directly via a bookmarked site or trusted app. Avoid links in emails and messages, even if the branding looks genuine.
Strong passwords and 2FA
Give each account its own long, complex password and store them in a reputable password manager. Turn on two-factor authentication wherever it is offered to add a second check at sign-in.
Safe network use habits
Secure Wi-Fi
Protect home and office Wi-Fi with a strong passphrase and modern encryption such as WPA2 or WPA3. Change default router credentials and disable unused remote access features.
Be careful on public Wi-Fi
Assume shared networks are untrusted. Avoid accessing sensitive accounts on public hotspots or use a trusted VPN when you must connect.
Keep everything updated
Apply operating system, application and firmware updates promptly. Patches close known holes that attackers routinely exploit.
Use spam and phishing filters
Enable filtering on your mail platform to quarantine suspicious messages and block known malicious senders and links.
Safe device use habits
Antivirus and anti-malware
Install reputable security software on computers and mobiles and allow it to update automatically. Enable real-time protection and regular scans.
Firewalls
Keep built-in firewalls enabled on endpoints and network devices. Where appropriate, add an additional software or hardware firewall to restrict unnecessary inbound and outbound traffic.
Treat links and attachments carefully
Do not open attachments or click links from unknown or unexpected sources. When in doubt, verify with the sender through a separate, trusted channel.
By building these habits into daily work, individuals and organisations make social engineering much harder to pull off. Awareness, simple checks and timely updates go a long way in a connected world.
Conclusion
Social engineering works because it targets people, not just systems. Attackers lean on trust, urgency and curiosity to push us into mistakes. Understanding those levers helps you spot the tell-tale signs and slow things down.
Keep learning, keep your defences current and talk openly about new scams with your team, friends and family. Small, consistent improvements in how we communicate, log in and verify requests reduce risk for everyone.