In this article
Welcome to the ever-evolving world of cyber forensics, a crucial and dynamic field at the intersection of technology and law enforcement. In the digital era, where our lives intertwine with technology at every turn, the importance of cyber forensics has surged dramatically. It’s a discipline that extends far beyond the realms of law enforcement, touching the lives of ordinary individuals and the operations of businesses worldwide.
Imagine a world where digital transactions, communications and exchanges are part and parcel of everyday life. Now, consider the vulnerabilities that come with such a digital existence – cybercrimes ranging from identity theft to corporate data breaches. This is where cyber forensics steps in as a guardian, unravelling the mysteries of digital crimes and safeguarding our digital landscape.
In essence, cyber forensics is not just about understanding the ‘bits and bytes’; it’s about piecing together the digital clues to protect and preserve the very fabric of our digital lives. It’s a journey through a landscape where technology meets law, order meets chaos and prevention meets cure. Welcome to the fascinating world of cyber forensics.
What Exactly Is Cyber Forensics?
Definition: At its core, cyber and digital forensics is the process of extracting, preserving and analysing digital evidence in a way that’s legally admissible. It’s a meticulous process that requires a deep understanding of various digital formats and legal protocols.
Types of Cyber Forensics
Cyber forensics encompasses various specialised fields. Each type focuses on a different aspect of digital data and plays a unique role in uncovering digital evidence. Understanding these types is key for professionals in the field and for businesses looking to strengthen their cyber security frameworks.
Database Forensics
This area involves the detailed analysis of databases and their related metadata. Forensic experts in this field scrutinise database logs, in-memory database contents, and other related data to track unauthorised database use, understand data manipulation, and recover deleted records. This is particularly crucial in cases involving data theft or tampering.
Email Forensics
Email systems are often the target of cybercriminals. Email forensics involves the recovery and detailed analysis of emails, including deleted messages and metadata. This can be pivotal in tracing the source of phishing attacks, identifying the senders of malicious emails, and uncovering the sequence of events in a cybercrime incident. It’s not just about retrieving data but understanding the context and intent behind communications.
Malware Forensics
Malware, or malicious software, is a common tool used in cyber attacks. Malware forensics involves dissecting malware to understand its origins, functionality and the extent of its impact. This field is vital in creating defences against new malware strains and in understanding the strategies and tactics of cybercriminals.
Memory Forensics
Memory forensics is about analysing volatile data in a system’s RAM. This can reveal invaluable insights about the state of a system during an incident, providing clues that are not available in non-volatile storage data. It’s particularly useful in investigating complex cybercrimes where the attacker has left little or no trace on the hard drive.
Mobile Forensics
With the ubiquity of mobile devices, mobile forensics has become increasingly important. This field involves recovering and analysing data from mobile devices, including call logs, messages, emails, and application data. It extends to the examination of GPS and location data, which can be crucial in tracing the activities and movements of individuals involved in cybercrimes.
Network Forensics
Network forensics focuses on the monitoring and analysis of computer network traffic. This can include the interception and analysis of data packets travelling over a network. It’s crucial for detecting and responding to intrusion attempts, understanding the nature of network-based attacks, and gathering evidence for legal proceedings.
Each of these forensic fields employs a combination of technical skills, specialised tools, and investigative techniques to uncover the truths hidden in the digital realm. They are interconnected and often overlap in comprehensive forensic investigations, offering a multi-faceted view of the digital evidence.
For businesses, understanding these types of cyber forensics is key to developing effective strategies for incident response and prevention, ensuring the cyber security and integrity of their digital assets.
The Cyber Forensic Process Unveiled
The process of cyber forensics is a detailed and structured journey through the collection, examination and interpretation of digital evidence. Each phase is critical, requiring a high level of expertise and precision to ensure the integrity and utility of the information gathered.
Let’s explore these stages in more detail:
Identification
Spotting Red Flags
The first phase of the cyber forensic process is all about detection. It involves identifying signs or anomalies that suggest a security breach or cybercrime. This could include unusual network traffic, unexpected changes in file sizes or types, or alerts from security systems.
Initial Assessment
Once potential indicators of a cyber incident are spotted, an initial assessment is crucial to determine the nature and scope of the breach. This step helps in prioritising the response and allocating appropriate resources.
Preservation of Scene
Crucial in this stage of data recovery is the preservation of the ‘digital crime scene’. It’s vital to ensure that no further data is lost, tampered with, or compromised. This might involve isolating affected systems or securing network logs to prevent data overwriting.
Collection
Gathering Evidence
The collection phase is about systematically gathering digital evidence. This could involve cloning hard drives, imaging affected systems, capturing network packets, and securing cloud storage data. The goal is to create exact replicas of digital evidence that can be used for forensic analysis without altering the original data.
Maintaining Integrity
Ensuring the integrity of the evidence collected is paramount. This involves using write blockers to prevent data modification, maintaining a chain of custody, and properly documenting every step of the process to ensure the evidence remains admissible in legal contexts.
Analysis
Utilising Forensic Tools
In the analysis phase, forensic experts use specialised tools to sift through the collected data. They look for deleted, hidden, or encrypted files; analyse file metadata; and reconstruct event timelines.
Data Reconstruction
A key aspect of this stage is reconstructing the sequence of events that led to the cyber incident. This involves piecing together digital artefacts to understand the methods and pathways used in the breach.
Identifying Perpetrators and Methods
The analysis aims to uncover evidence of not only how the breach occurred but also potentially who was behind it. This can involve tracing digital footprints, examining network logs and analysing malware used in the attack.
Reporting
Documenting Findings
The culmination of the cyber forensic process is a comprehensive report that documents the findings. This report should detail the methodology used, the evidence found, and the conclusions drawn.
Clear and Understandable Presentation
It’s important that the report is not only thorough but also clear and understandable, even to those without technical expertise. This may include summaries, graphs, and other visual aids to elucidate the findings.
Recommendations & Next Steps:
A crucial component of the report is the recommendations for future action. This might include suggestions for improving security measures, changes to policies, or recommendations for legal action.
The cyber forensic process is a blend of technical expertise, methodical investigation and legal acumen. Each stage plays a critical role in building a clear and comprehensive picture of a cyber incident, aiding in both the resolution of current issues and the prevention of future breaches.
The Rising Importance of Cyber Forensics
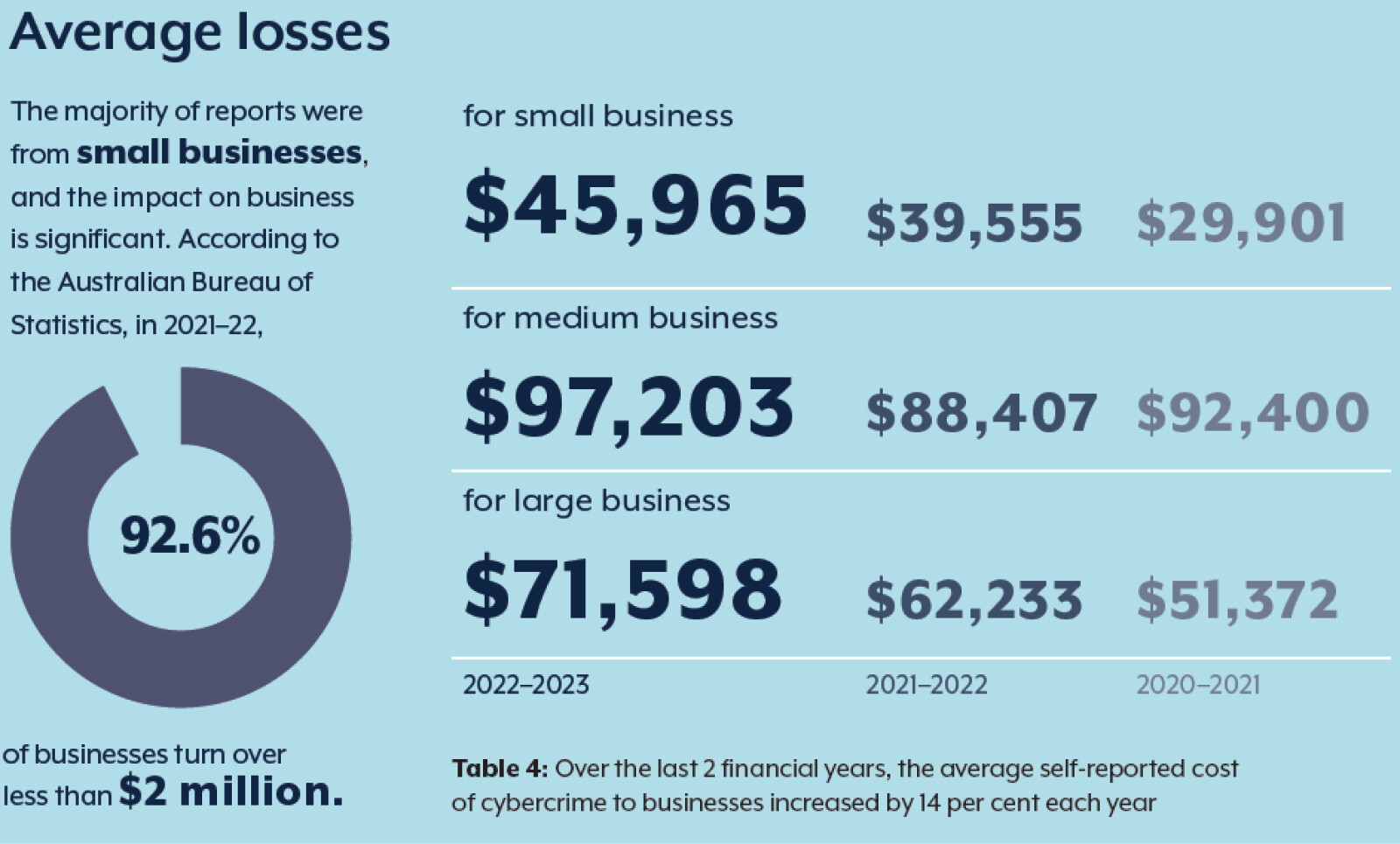
For businesses, the stakes are particularly high. In an age where a single data breach can cost millions and tarnish a company’s reputation irreparably, understanding and implementing cyber forensic practices is not just an option but a necessity. It’s about protecting not just data but the very essence of business integrity and customer trust.
And the need for cyber forensics has never been greater. High-profile cybercrimes, like the infamous Equifax breach, demonstrate the sophisticated nature of modern cyber threats.The breach not only led to significant financial losses for Equifax but also impacted millions of individuals, exposing their personal information. This high-profile case underscored the critical role of cyber forensics in both post-breach analysis and preemptive threat detection.
With regulations like the General Data Protection Regulation (GDPR) in Europe and various data protection laws evolving worldwide, businesses face not only regulatory fines but also the prospect of litigation in the event of a data breach. Cyber forensic practices are vital in ensuring compliance with these regulations and in providing necessary documentation and evidence in legal proceedings.
Enabling a Proactive Approach to Cyber Security
However, the need for cyber forensics is not just a reactive process, it’s increasingly becoming proactive. As cyber threats evolve, so does the role of cyber forensics in identifying potential vulnerabilities, assessing risk exposure and developing robust cyber security strategies.
This proactive approach not only mitigates the risks of future breaches but also aligns with current best practices for corporate governance and cyber risk management.
Identifying Potential Vulnerabilities
Proactive cyber forensics involves continuous monitoring and auditing of systems to detect and address vulnerabilities before they are exploited. This includes regular assessments of network infrastructure, software applications and data storage practices. By identifying weak spots, businesses can fortify their defences, reducing the likelihood of successful cyber attacks.
Assessing Risk Exposure
A key element of a proactive approach is the on-going evaluation of the company’s cyber risk profile. This involves analysing not just the technical aspects of a company’s cyber security posture but also the human and procedural elements of the organisation.
Cyber forensics plays a crucial role in that risk assessment, providing insights into potential threat vectors and the effectiveness of current security protocols, as well as the legacy elements and learning from previous breaches
Developing Robust Cyber Security Strategies
The insights gained from cyber forensic analyses are invaluable in shaping comprehensive cybersecurity strategies. These strategies should encompass not only technical solutions like firewalls and encryption but also training programs for employees, incident response plans and regular updates to security policies. A proactive approach means staying ahead of the curve, anticipating new types of cyber threats and preparing accordingly.
Pursuing a Career in Cyber Forensics
The field of cyber forensics offers a range of exciting career opportunities. These positions are crucial in the fight against cybercrime and in protecting digital assets.
Here’s a list of key jobs in this dynamic field:
Forensic Computer Analyst
These professionals are at the forefront of recovering and analysing data from digital devices. They are essential in uncovering digital evidence for criminal and civil investigations.
Cyber Security Analyst
This role involves protecting systems and networks from cyber threats. They collaborate closely with forensic digital investigation teams, particularly in the aftermath of cyber incidents, to enhance security protocols.
Incident Responder
Specialised in rapid response to security breaches, Incident Responders are crucial in mitigating the damage of cyber attacks, analysing breaches and aiding in recovery efforts in real-time.
Digital Forensic Investigator
Often working with law enforcement or private sectors, these investigators focus on crimes involving digital platforms, gathering evidence crucial for legal proceedings.
Generally speaking, professionals must combine technical proficiency in computer systems, networks and software with sharp analytical thinking and meticulous attention to detail.
Essential skill sets for the field include problem-solving, a solid understanding of relevant laws and regulations, effective communication and a strong ethical foundation.
The Final Byte
Cyber forensics is no longer a niche field, it’s a critical component of the modern cyber security landscape. Its importance in identifying, understanding and preventing cybercrime cannot be overstated.
For businesses, incorporating cyber forensics into their cyber security strategy is not just advisable; it’s imperative to maintaining a robust and up to date cyber security posture.
As we navigate an increasingly digital world, the role of cyber forensics will only grow in significance, offering both challenges and opportunities to those willing to delve into this dynamic field.