In this article
The Australian Cyber Security Centre (ACSC) launched its flagship Annual Cyber Threat Report on 4 November 2022 in collaboration with the Australian Criminal Intelligence Commission and the Australian Federal Police.
Here are the key takeaways from the ACSC 2022 Threat Report, and what the ACSC is doing to respond to the current and future Australian cyber threat environment.
Update: Please our review of the 2023 ASD Cyber Threat Report for the latest takeaways on the Australian cyber security threat landscape.
The frequency, cost & severity of cybercrime is increasing
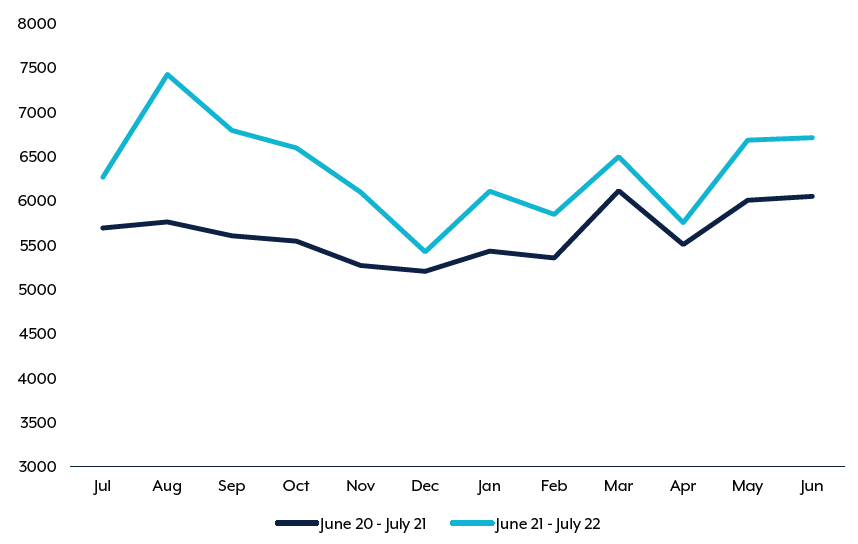
During the 2021–22 financial year the Australian Government online cybercrime reporting tool, ReportCyber, received over 76,000 cybercrime reports. That’s approximately one every seven minutes, and an increase of 13% on the previous year.
And with the rate of cybercrime increasing, so too is the cost. Businesses bore the brunt of the costs, with the average cost per cybercrime report rosing to over $39,000 for small business, $88,000 for medium business, and over $62,000 for large business.
Instances of business email compromise increased in severity, with an average loss of $64,000 per report, and the number of publicly reported software vulnerabilities increased by 25%.
This was evidenced in a marked increased in calls to the ACSC’s Cyber Security Hotline, which rose by 15% from the previous year to over 25,000 calls—an average of 69 per day.
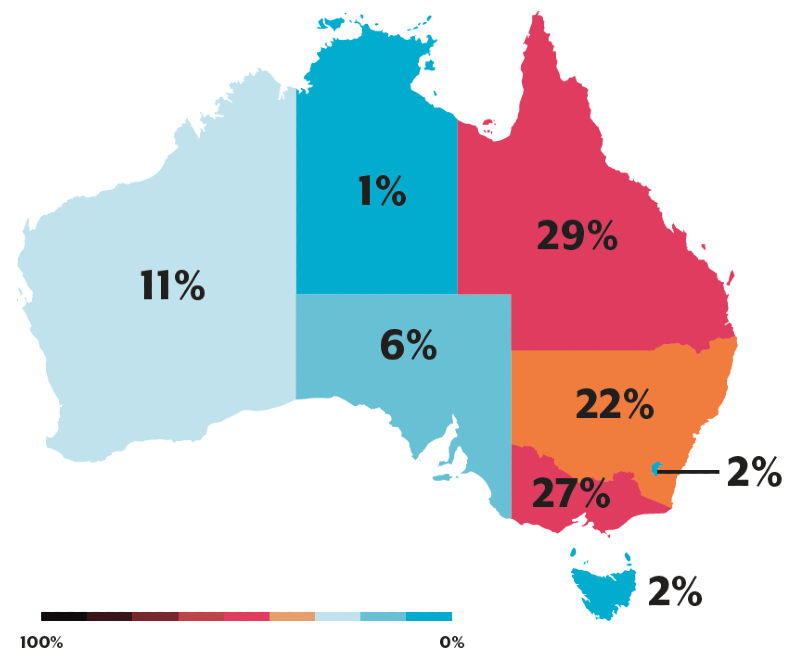
Queensland and Victoria reported the highest rates of cybercrime. The highest average losses were experienced by the Northern Territory, with an average of over $40,000 per cybercrime where a financial loss was incurred. Next in line was Western Australia, with an average of over $29,000 per crime.
The key cyber security threats of 21-22 were all cyber-enabled crimes. Online fraud accounted for 26.9% of all cybercrime reported, crime related to online shopping 14.4%, and crime related to online banking 12.6%.
As well as costs, cyber incidents reported are increasing in severity. Incidents of extensive system compromise made up 15% of all reported cyber security incidents, up 6% from the previous year, and there was a noted increase in attacks on large organisations.
Interestingly, ransomware only made up a tiny percentage of total cybercrime reports, at 0.59%. Despite this, the ASCS determined that ransomware had the biggest impact on its victims, due in part to business disruption following data encryption, and the reputational damage that the businesses can receive.
The ACSC Cyber Threat Report note these as the most common cyber security threats of 21-22.
Ransomware dominated
Ransomware was one of the key cyber threats that Australians faced.
But the ACSC Annual Cyber Threat Report noted a change in the ransomware business model. Rather than a once-and-done approach, cybercrime groups are now sharing victim information to other entities, increasing their vulnerability through follow-on targeting. This combination of data encryption and the threat to publicly release sensitive information is known as ‘double extortion’
Users also faced ‘multifaceted extortion.’ This sees extra elements included in the attack, such as criminals convincing third-party stakeholders into pressuring the original victims into negotiation, or sustained DDoS attacks against their network during the ransom negotiations.
In 2021–22, ransomware groups stole and released the personal information of hundreds of thousands of Australians, with costs extending beyond the ransom demands. These included system reconstruction, lost productivity, and lost customers.
ReportCyber received 447 ransomware related cybercrime reports, a 10% decrease on the previous year. It’s noted that there’s the likelihood of a significant underreporting on ransomware attacks, particularly from victims who refuse to pay a ransom. A 2022 study published by the Australian Institute of Criminology corroborates this, finding that only 19% of ransomware victims seek a ransomware removal service, advice or support from the police or the ACSC.
Of these 447 reports, the ACSC responded to 135 cyber security incidents related to ransomware—a 75% increase from the previous financial year.
While all sectors of the Australian economy were directly impacted by ransomware, the top five reporting sectors accounted for 47% of all ransomware-related crime. The education and training sector received the largest number of incidence, thanks to the continued increase in remote learning and personal device use among employees working remotely.
Business email compromise is big business
Business email compromise (BEC) gives cybercriminals the ability to go directly to the source. The ACSC Annual Cyber Threat Report notes that it’s still a lucrative space for cybercriminals, and one of the key cyber threats.
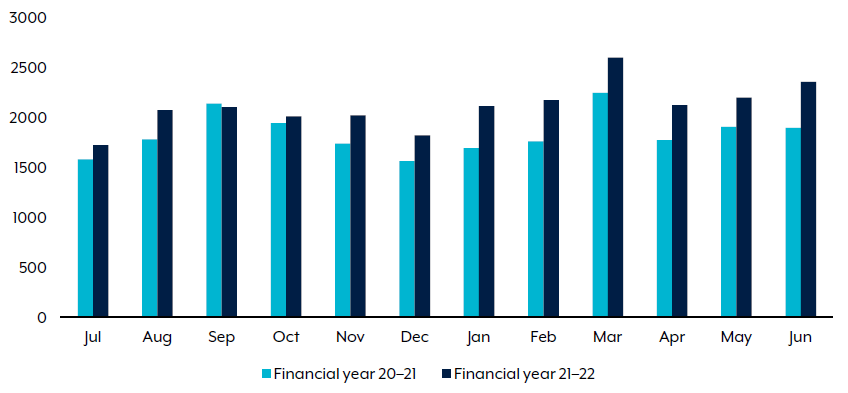
While the number of successful BEC reports declined slightly to 1514, the overall self-reported losses throughout the year increased significantly to over $98 million. The national average loss per successful BEC increased to over $64,000.
Queensland had the most BEC reports (389 reports), and Western Australia had the largest self-reported losses, at approximately $112,000 per report. The State also experienced a number of individual instances seeing financial losses of over $1 million, lifting the overall average.
Investigations into BEC suggest that property settlements were increasingly being targeted, a trend that’s likely to continue.
The increasing threat to critical infrastructure
The ACSC Annual Cyber Threat Report outlines how 2021-22 saw infrastructure networks globally come under threat, with Russian-aligned cybercrime groups starting to target Australian infrastructure.
This has caused ACSC to reshaped its definition of ‘critical infrastructure.’ Under this new definition, around 25% of all cybercrime incidents in 20-21 affected critical infrastructure. In 21-22, 8% of fraud cybercrime incidents impacted critical infrastructure—which is still an alarming 98 incidents.
The key takeaway is that all Australian organisations should report cyber security incidents, regardless of their reporting requirements or scope of the attack and maintain modern and up to date IT infrastructure. This helps to increase the visibility of cyber security threats, increase ACSC’s understanding of them, and help to support mitigation in the future.
Vulnerabilities are more vulnerable
The past year saw the attack landscape broaden considerably. The number of recorded software vulnerabilities increase by 25% over the previous financial year.
Over 24,000 Common Vulnerabilities and Exposures were identified, and included high-impact vulnerabilities, such as in Microsoft Azure and Log4j.
The time between vulnerability disclosure and exploit is closing rapidly, too. With better technology and more tools as their service, what once took weeks to uncover and exploit is now taking experienced cybercriminals just days, or even hours.
More and more, cyberspace is becoming a battleground
State actors across the world have continued to find innovative ways to deploy online attacks.
In 21-22, Australia was the target of persistent cyber espionage from a wide range of malicious cyber actors. This isn’t particularly surprising, given Australia’s international partnerships and participation in multilateral forums.
But despite the range of technologically devastating platforms available to cyber criminals, the ASCS observed that relatively simple tools and techniques were often the most effective. Tried-and-true methods like spearphishing, targeting third-party service providers, or using public vulnerabilities to exploit vulnerable targets like unpatched or misconfigured systems, were all considered urgent and critical threats attack against Australian targets. The ACSC expects state actors to continue using these methods, as long as it’s financially viable.
Waging war in cyberspace has been increasingly used as a geostrategic tool, allowing state actors to steal security secrets and intellectual property from opposing countries, or sow disinformation among the general public.
Yet another shot heard around the world
Cyber operations have been increasingly used as a tool of war alongside ground-based offensives, and Russia’s invasion of Ukraine had impacts all over the world.
Ukraine experienced an onslaught of sustained disruptive malicious cyber activity, including distributed denial of service (DDoS) attacks. In the first six weeks of the invasion at least eight variants of destructive malware were identified.
One large-scale Russian cyber operation on 24 February saw over 10,000 satellite communications terminals outside Ukraine disabled. These terminals supported wind turbines and internet services for the country.
This integration of cyber operations into conventional war has and will continue to impact non-combatants, and Australia isn’t immune. The ACSC Annual Cyber Threat Report noted that Australia will be vulnerable to major supply chain attacks, and given our size, resource money, and international relationships, this makes us a particularly attractive target.
Cybercrime is evolving and advancing
Australia remains an attractive target for cybercriminals. During the 2021-22 period fraud, financial and identity theft, and business email compromise continued as common cyber threats.
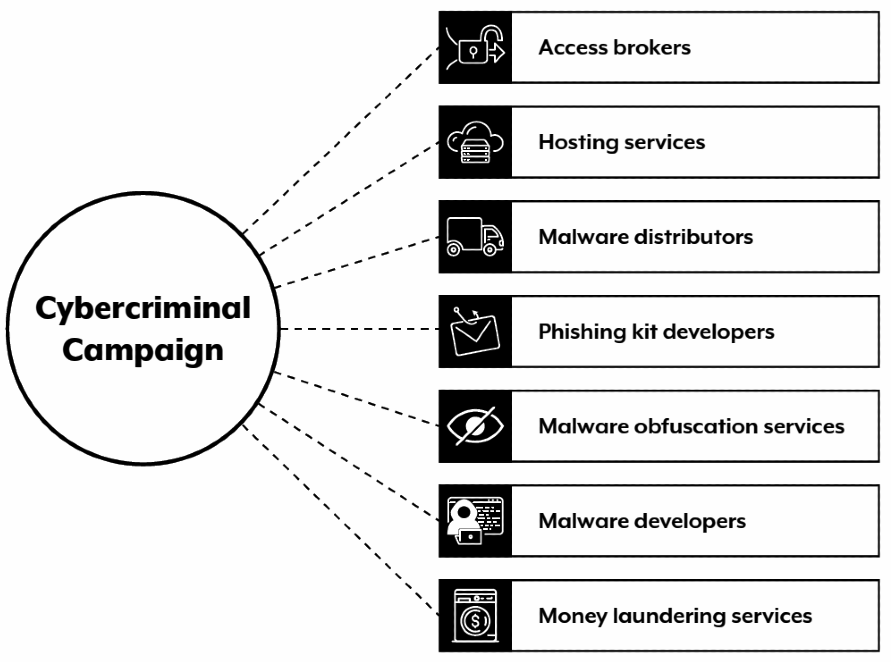
Alarmingly, the nature and complexity of these attacks evolved, and became more sophisticated. The range of tools, services, and information available to purchase proliferated, lowering the barrier to entry for cybercriminals.
Cybercrime-as-a-Service increased the overall threat to Australia, and has allowed skilled cyber criminals to monetise their skillsets.
Ultimately, we’re more susceptible to cyber security vulnerability than ever
Thanks to the virtualisation of Australian life, interconnectivity has increased dramatically. Which, in turn, has increased cyber security risks.
With a large proportion of Australian workers regularly still working from home, we’re opening ourselves up to more attacks. Many personal devices, such as modems, routers, and storage, are insecurely designed with minimal security maintenance. They feature insecure firmware, hardcoded backdoors, and inconsistent patching. In fact, most home-based routers manufactured before 2017 don’t automatically update their firmware.
The Internet of Things is growing rapidly, introducing new types of vulnerabilities. As such, malicious actors are looking at new ways to compromise multiple victims across a range of sectors from a single entry point.
21-22 saw multiple MSPs targeted, as they’re used by businesses of all sizes, in all sectors. Supply chains were also a priority target, a trend that ACSC expects to continue.
So, what can be done?
To combat the evolution of the cyber threat landscape, ACSC is undertaking a range of initiatives to help Australians remain secure against increasing cybercrime.
ACSC deployed five successful operations against online marketplaces and foreign scam networks, to combat Cybercrime-as-a-Service.
The Australian Federal Police led a taskforce to perform Operation Dolos, working with individual Australians and small-to-medium businesses that have been targeted by email compromises. They were able to arrest 18 money mules, and recover over $5.97 million in funds stolen by cybercriminals.
REDSPICE
Australian Signals Directorate (ASD) deployed REDSPICE, its most significant investment in 75 years. Standing for Resilience, Effects, Defence, Space, Intelligence, Cyber, Enablers, REDSPICE is a project that’s designed to address future cyber threats and further strengthen our cyber defences.
It’s expanding the range and sophistication of Australia’s cyber intelligence, and offensive and defensive capabilities, and provides better resources that allows ASD to:
- anticipate and prevent crises;
- block cyberattacks against critical infrastructure;
- equip government with options for retaliatory cyber actions;
- improve Australia’s cyber resilience;
- train 1900 new cybersecurity roles;
- increase ASD’s global footprint by four times; and
- provide $5 billion in opportunities for Australian industry to grow the cyber security sector.
CTIS
The ACSC launched a new initiative, the Cyber Threat Intelligence Sharing platform. It went live on 1 November 2021, and enables the sharing of cyber threat intelligence between ACSC partners at machine speeds, with automated delivery of information in a timely, structured manner. Allows the ACSC to receive information on suspicious cyber activity that they wouldn’t otherwise have visibility over.
Australian Protective Domain Name System
The Australian Protective Domain Name System (AUPDNS) is an initiative dedicated to protecting government networks. It uses verified threat intelligence to build a block list of known malicious web domains. It monitors connections, stopping access to malicious sites, while also stopping malware currently infecting devices from communicating with their orchestrators.
In 2021–22, AUPDNS processed over 36 billion queries, and blocked over 24 million domain requests. 171 organisations came on board, including a number of state and local government agencies.
Domain Takedown Service
The Domain Takedown Service pilot launched in 2021. Works to detect suspicious malicious software, verifies their severity, then, depending on the outcome, issues a takedown notice for the domain.
The Service also created 10 ‘honeypot’ servers that gives ACSC the ability to directly report malicious domains for manual verification and takedown by itself.
Promoting cybersecurity literacy and preparedness
The ACSC is also conducting a suite of transformation activities to increase information sharing and reporting, and grow the scale and maturity of business, organisational, and individual cyber security practices. It aims to promote better cyber security through robust cyber incident detection and response, business continuity, disaster recovery planning, and ultimately create an avenue to reduce demand on the ACSC’s finite response capabilities, while putting the power back into the user’s hands.
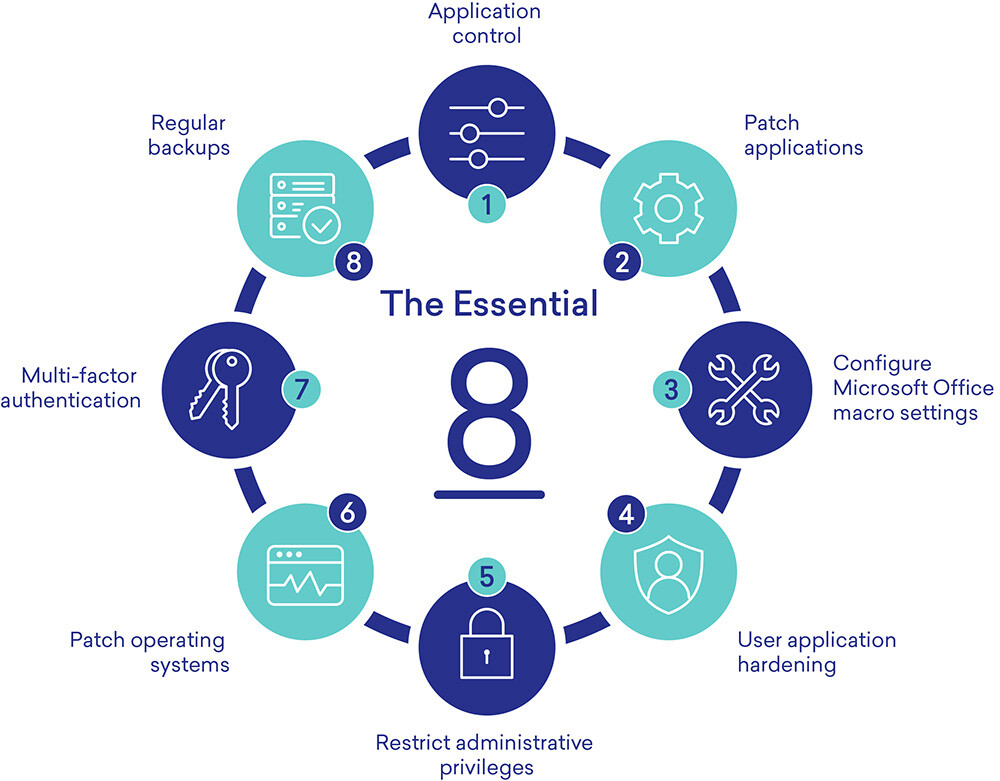
To achieve this, ACSC recommends that businesses deploy appropriate cyber security measures, starting with the Essential 8, and partner with them to help improve their cyber security exercises and resilience across the country.
To date, they note that literacy has increased since the previous year. It’s jumped 65% for Business Partners, and 8% for Home Partners.
Despite this, there’s more work to be done.
Protect your business against the evolving threat landscape
While it may seem like doom and gloom, the Australian Cyber Security Centre Annual Cyber Threat Report actually gives us hope. It demonstrates that while cybercrime is increasing, so too is the maturity and capability of Australia’s cybersecurity defences.
TechBrain is a leading provider of innovative IT security solutions for businesses—and we’re here to help your cybersecurity evolve too. Get in touch with us today to discuss your business’ network and cyber security matters, access our expert cyber security advice, and see how we can help you boost your security environment against current and future cyber threats.